Pentest or real threat? How automated investigations help you respond in record time
Why did the security team go to art school? To become better pen testers.
Is it a drill or a real cyber attack? Security teams face this question all too often, usually under high pressure. But what if you could quickly differentiate penetration tests — the mock cyber attacks designed to test an organization’s defenses — from real threats in the cloud? Thanks to the latest innovation from Lacework, the guesswork is over. Let’s take a closer look at how the Potential Penetration Test Composite Alert works and the impact it could have on your operations.
How does it work?
This new Composite Alert blends anomaly detection, signature-based identification, and behavioral analytics to accurately distinguish penetration tests from real cloud threats. By analyzing host activity, it identifies genuine threats, integrating seamlessly with existing correlation methods. This reduces alert fatigue and enhances clarity for security analysts.
A treasure trove: Why the pentest alert findings are valuable
Whether it’s identifying unseen vulnerabilities or gaining risk insights, this new alert aids security teams in several key areas:
- Vulnerability management: This alert ensures you’re the first to know when pentesters take advantage of an existing vulnerability. Along with pentesting insights, this enables you to strengthen your defenses before real danger strikes..
- Incident response: By cutting through the noise of scripted attacks, this alert prepares your team to quickly identify and respond to real threats.
- Compliance made easy: This alert helps you meet compliance requirements with confidence.
Red-colored glasses: Differentiating from real attacks
With this new alert, Lacework tells the story behind the actions, distinguishing between a red team practice session and a real threat. It reads the digital body language, discerning controlled testing from unpredictable attacks.
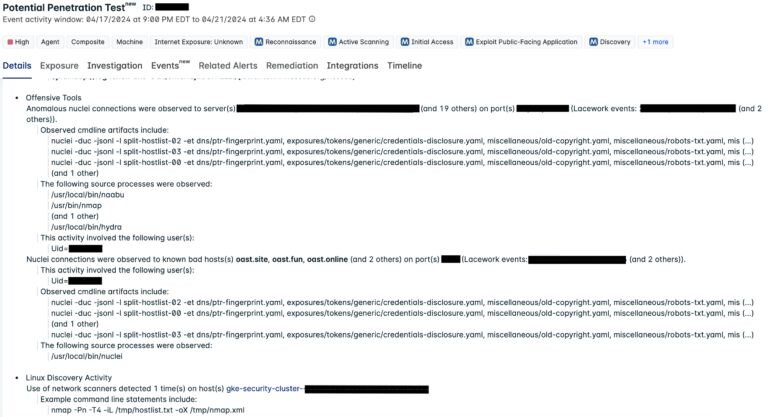
Here’s an example from a recent alert:
Alert and ready: 5 steps to handle a potential pentest
So, when you see this Composite Alert, what do you do next? Here’s a structured approach to effectively manage the situation when Lacework flags a potential penetration test:
1. Confirm the nature of the activity
Start by determining the origin and purpose of the activity. This involves checking with your security team or system administrator to ascertain whether the detected activity is part of a scheduled penetration test (often referred to as a “red team” exercise) or if it represents a genuine security threat. This step is crucial as it dictates the subsequent response strategy. If it is an authorized test, you should have records or a notification system indicating such activities. If no such evidence exists, treat the activity as a potential security breach.
2. Evaluate the scope and impact
Once the nature of the activity is verified, assess the extent and potential impact of the simulated intrusion. This involves analyzing which systems are affected, the type of data at risk, and the methods used by the testers. This step is essential for understanding the severity of the situation and helps in formulating an effective response. It’s also important to assess the sophistication of the tactics employed, as this information can provide valuable insights into the capabilities of the testing team or a potential attacker.
3. Manage the response appropriately
Confirm that the exercise is being conducted within the pre-defined parameters set for penetration testing. Coordinate with the team responsible to ensure that all activities are controlled and documented, and verify that the test does not exceed authorized boundaries or cause unintended damage. If an actual attack is suspected, immediately escalate the situation according to your incident response plan. Secure the affected systems to prevent further damage and begin mitigation processes.
4. Document and analyze
Maintain thorough documentation throughout the simulated incident. This should include logs of all detected activities, actions taken during the response, and any communications related to the incident. In a real attack, detailed records are invaluable for post-incident analysis and for legal or compliance reasons. They also serve as a factual basis for understanding attack vectors, successful defenses, or vulnerabilities exploited.
5. Strengthen defenses
Use the insights gained from the penetration or red team test to improve your security posture. This includes updating response strategies, enhancing security protocols, and implementing new defenses based on the vulnerabilities uncovered and the tactics employed by the testers. This stage often involves revisiting your threat models and security assumptions, conducting additional training for your security personnel, and deploying updated tools or patches to thwart similar future attempts.
See how Lacework can help
This new alert will help your security teams prioritize their time in the most impactful way so your organization can focus on what it does best.
See for yourself how Lacework helps detect penetration tests and the latest threats with our patented approach. Get complete access to our platform with our 14-day free trial here.
Categories
Suggested for you