Breaches happen: How cloud security platforms like Lacework save the day
The cloud has given developers the power to innovate quickly and spin up resources in minutes. But with constantly changing cloud environments, it’s easy to make a simple configuration mistake and unknowingly expose your business to attacks. The catch-22 here is that moving fast is the only way to avoid being disrupted by a newcomer in your respective market. This creates diametrically opposed goals for your software engineering and security teams.
To maintain innovation while staying secure, your security platform needs to adapt and progress at the same rapid rate as your technology. But how do you know if your security platform can keep up?
To explain the game-changing benefits that a cloud security platform can provide, we’ll break down how a new initiative led to a cloud security breach at a fictitious company called Interlace Labs.
The power of behavior-based threat detection
One of the goals of cloud security is to detect, contain, and remove threats in your environment. While that seems simple, cloud activity logs and workloads generate massive amounts of data; at cloud scale, processing this amount of data becomes impossible for humans. To handle the workload, the only solution is to rely on automation and systems to analyze data efficiently. And because of the infinite number of possible attack vectors, leveraging behavior-based threat detection becomes necessary as it is impossible to predict what could happen in the cloud and write a rule or policy to detect every potential threat. Fortunately for Interlace Labs, they were using Lacework during an attack on their cloud.
The wrath of Khon: Security platforms vs. attackers
Interlace Labs’ breach problems begin with a contractor (aptly named Khon Traktour) that was employed to help develop a new groundbreaking project. As part of his workload remit, the contractor was given access to an Elastic Compute Cloud (EC2) instance and a Relational Database Service (RDS) cluster in AWS. After several hours, Khon developed a minimum working product for the new business application and then logged off for the day. Unfortunately for Interlace Labs, the software used to build this new application has critical vulnerabilities. Within hours, attackers discover this internet-exposed instance and its weaknesses. From there, they actively compromise the host.
The first indication of compromise came from a composite alert (Figure 1) that automatically correlated multiple security findings into a single alert. The alert shows that the attacker escalated privileges after escaping from a vulnerable container. They then began to execute discovery activities and established a reverse shell to their own network domain.
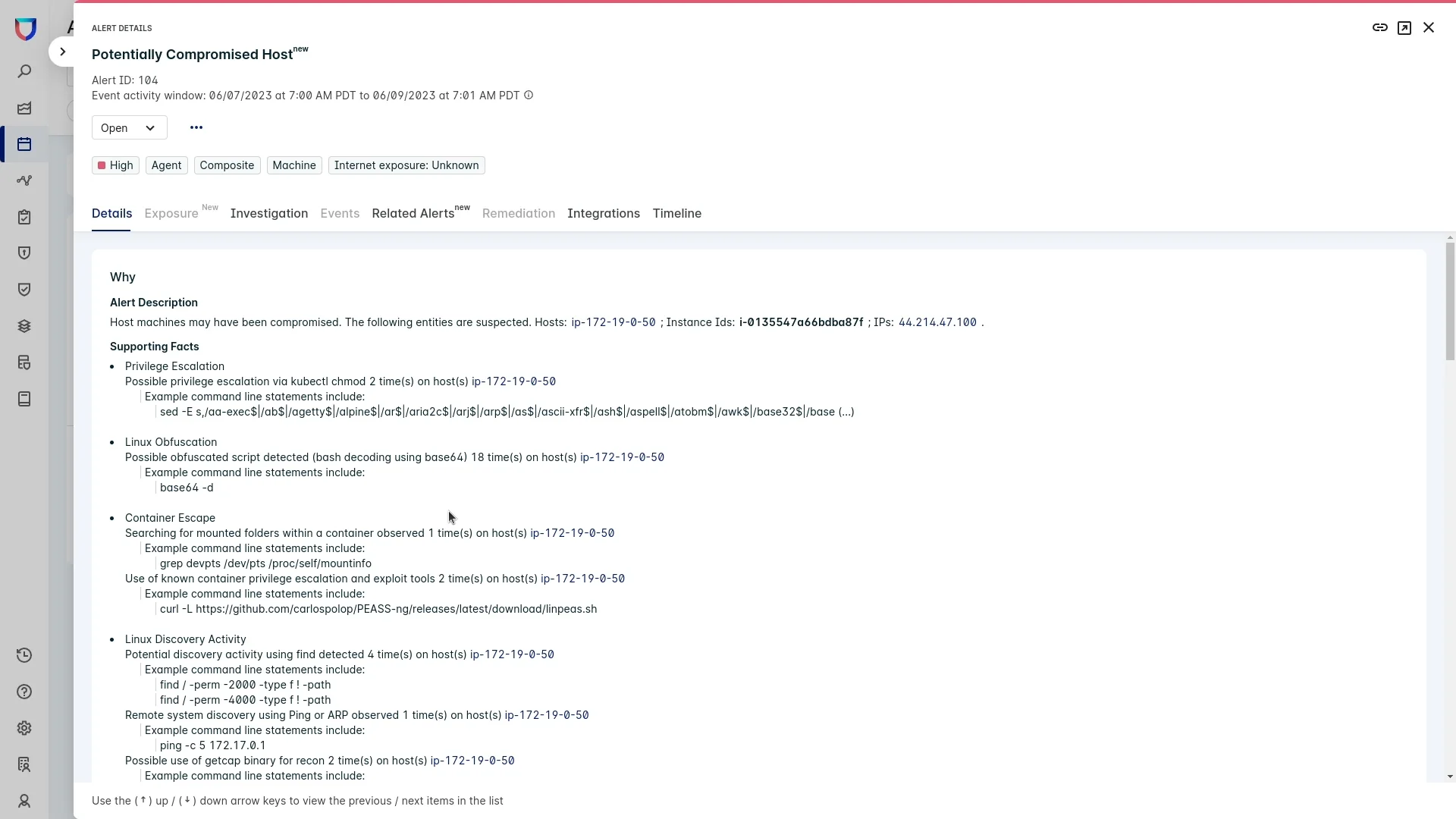
Figure 1: A composite alert shows an attacker escalated privileges and established a reverse shell to their own network domain
The attacker also discovered access keys in this host, which they then used to run discovery API calls across many different regions in the AWS account. Luckily for Interlace Labs, this behavior is out of character for this set of AWS access keys. Because Lacework learns the typical behavior of your cloud activity and workloads, it alerts customers when new, anomalous activity begins to occur. Lacework raised an additional composite alert for potentially compromised keys (Figure 2). The evidence gathered was then automatically correlated and presented to the security team with complete context so they didn’t need to waste time hunting through logs.
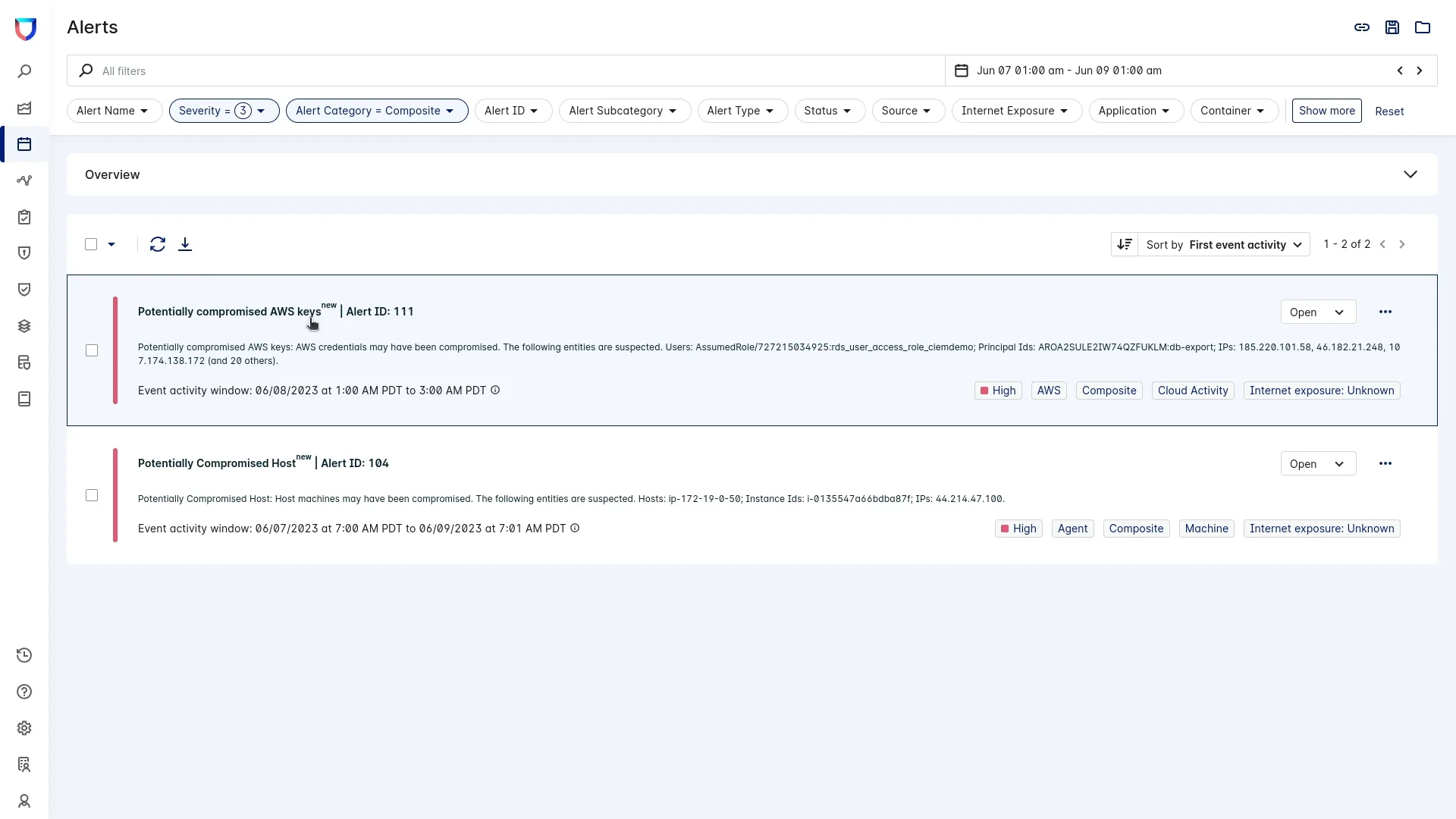
Figure 2: A composite alert shows potentially compromised keys
The attacker has compromised a host and is now using AWS access keys to see what they can do in this cloud environment. But with every single API call logged (thanks to CloudTrail), the attacker is now leaving footprints. With those access keys, the attacker finds and assumes a privileged role. And with these additional privileges, they begin targeting data to steal and potentially leverage for ransom. But leveraging the power of the Lacework Polygraph® Data Platform, the security team can easily visualize what this malicious user has done.
In the Polygraph visualization below (Figure 3), it appears that the threat actor is attempting to exfiltrate data by creating database snapshots of the RDS cluster that Khon Traktour used during his application development. On another platform, it would be a challenge for security engineers to continuously ingest and analyze these terabytes of data looking for the needle in the haystack – Lacework, however, makes these threats easy to see.
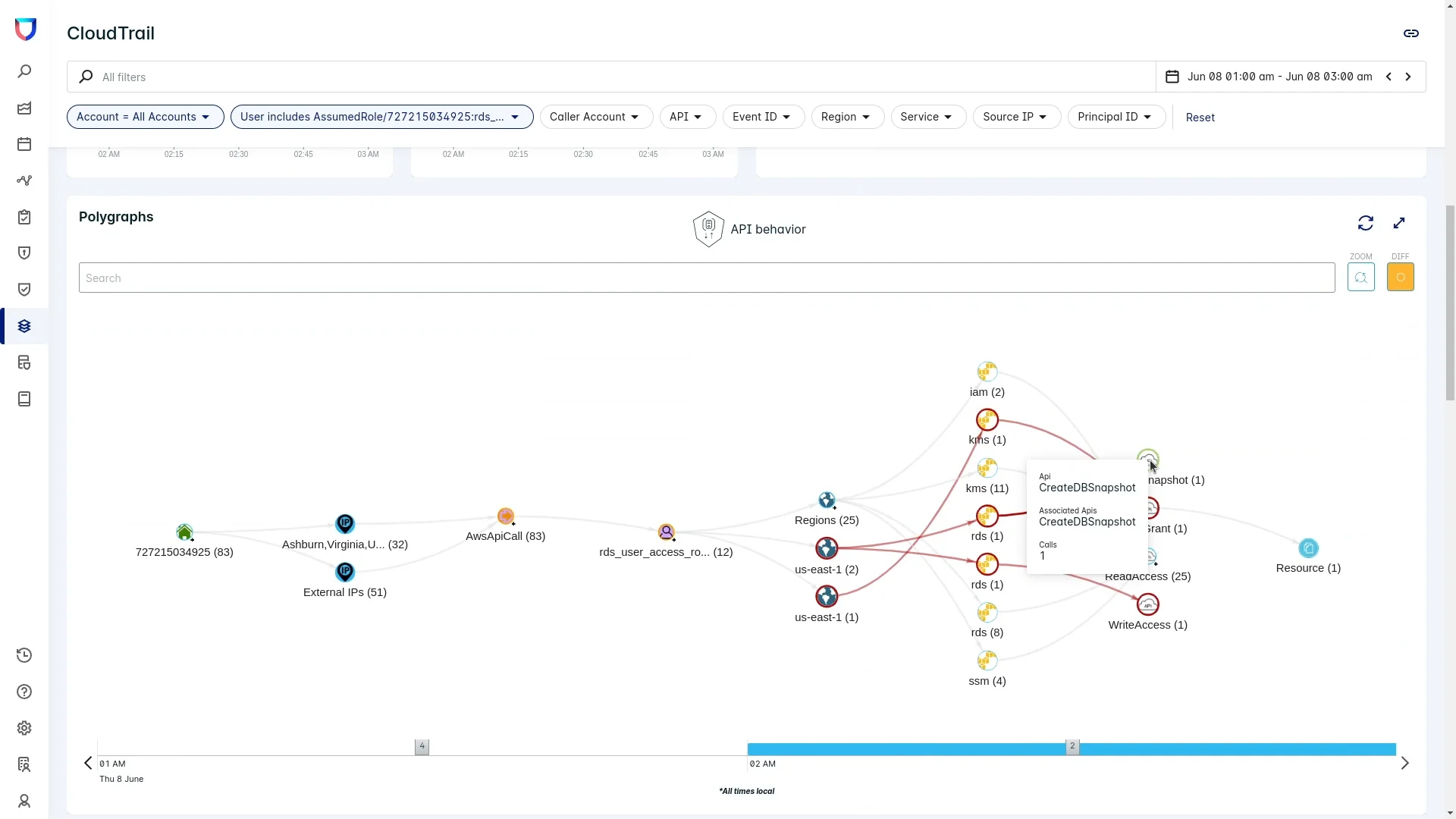
Figure 3: The Polygraph shows the threat actor attempting to exfiltrate data
Now that the threat has been detected and all the breach activity has been highlighted, it’s time to contain and remove the threat from the Interlace Labs environment. The security team quickly quarantines the host by removing its internet access and the keys for Khon Traktour are disabled. But any good security team won’t stop there. The immediate threat has been addressed and now they can focus on more proactive measures to prevent it from occurring again. And they can leverage the Lacework platform to do this with ease.
The battle is won, but the war wages on
Because we know that the host breach led to compromised credentials that gave access to a highly privileged role, it’s a no-brainer to begin investigating cloud identities and identity and access management (IAM) roles to address any excessive risk that could lead to future security incidents. To do so, Interlace Labs uses the newly announced Lacework CIEM capability. With CIEM, Interlace Labs can quickly identify their top identity risk such as active access keys that haven’t been rotated in six months, identities with full admin privileges, identities with key exposure, and more.
In the case of this incident, Interlace Labs can use the entitlements management explorer (Figure 4) to assess risk related to the RDS IAM role that was assumed by the attacker. There, it’s easy to see the risk score, risk categories, linked identities, and the resources or services this role has accessed versus the permissions that were granted based on actual cloud activity data.
This analysis highlights that the role has excessive usage permissions. Although this presentation of identity data seems simple, it is a very complex task. Through the process, the analysis collects an inventory of all identities in the cloud, assesses their net-effective permissions, and compares those permissions to activity data to implement the principle of least privilege. Interlace Labs uses Lacework to do all of this heavy lifting.
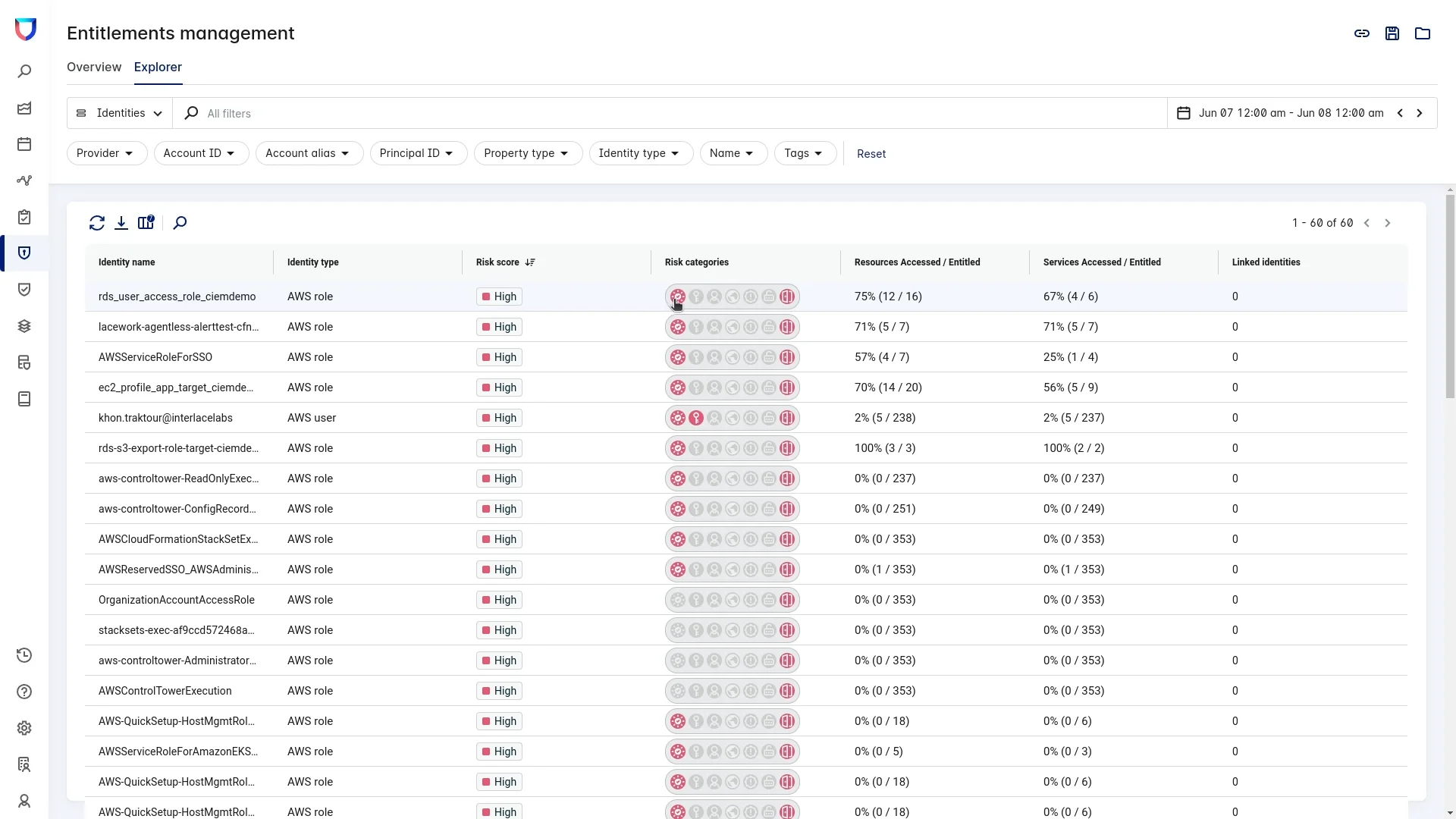
Figure 4: The entitlements management explorer shows the identity types and risk scores for each user
In addition to assessing the role used to create DB snapshots, Interlace Labs also uses the entitlements management explorer to understand the risk associated with the Khon Traktour AWS user. Not only does the security team at Interlace find that during an agentless scan of the host, the AWS access keys for Khon were hardcoded (which the attacker discovered and leveraged), they also get detailed remediation guidance to revoke the assumeRole policy of the AWS user that would prevent those hardcoded keys from being used to escalate future privileges. This continues the efforts around applying the principle of least privilege and enhances Interlace Lab’s overall security posture.
Reinforce your defenses to prepare for the next attack
Interlace Labs wants to continue their proactive security initiatives and can move from identity risks to vulnerability risk using the Lacework cloud security platform. In the attack path dashboard (Figure 5), they are presented with a prioritized list of risks that include vulnerable hosts, risky container images, attack paths with exposed secrets, and risky data assets. Looking at the dashboard, it’s clear that the host that was compromised was listed because it had vulnerabilities, hardcoded keys, and access to RDS.
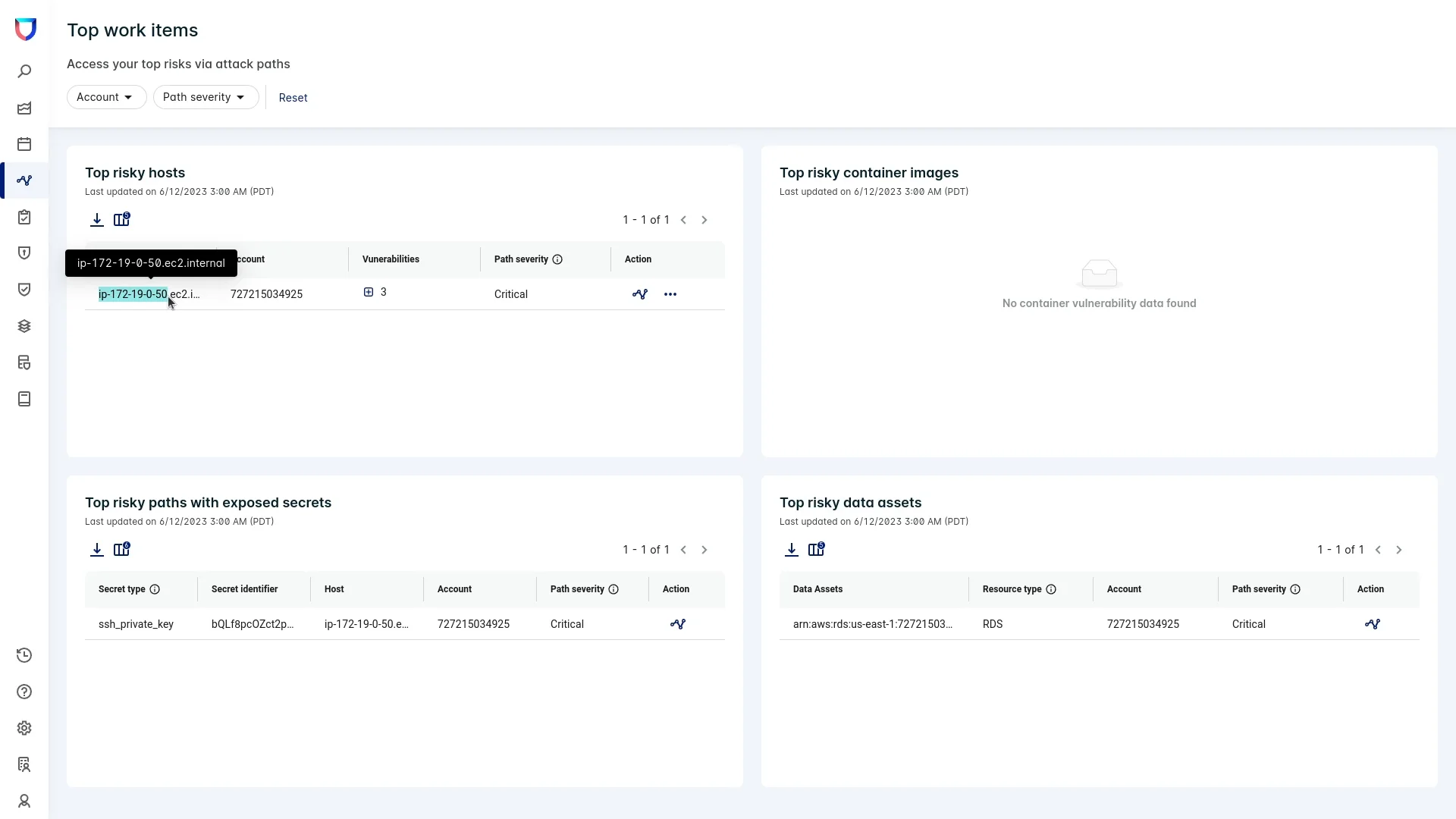
Figure 5: The attack path dashboard shows a prioritized list of risks
Taking a lesson from Interlace Labs, it’s easy to see the importance of viewing a complex cloud environment through the eyes of an attacker to stay ahead of potential breaches. Lacework delivers attack path analysis (Figure 6) by tying together multiple risk factors such as internet-exposed hosts or containers, critical vulnerabilities, misconfigurations, exposed secrets, identity risks, and other key metrics. For Interlace Labs, clicking into a path investigation from their top risks dashboard crystalizes the set of security risks the attacker leveraged in their breach. The host was exposed to the internet (a potential misconfiguration) and had several other issues such as vulnerabilities, hardcoded secrets, and excessive permissions. The attack path also shows the direct connectivity to the RDS cluster the attacker targeted for data exfiltration.
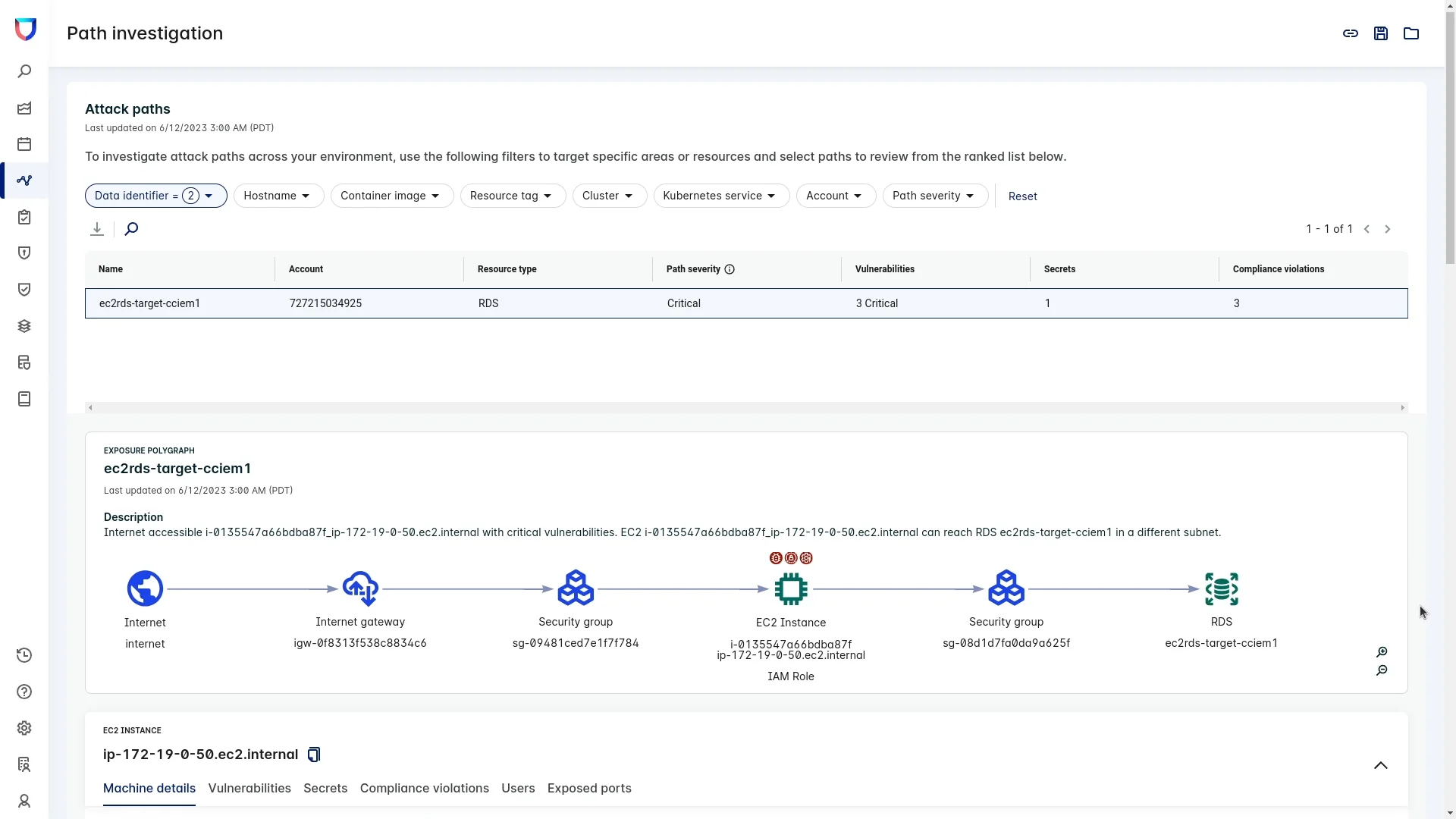
Figure 6: Attack path analysis connects risk factors so you can view your environment through an attacker’s eyes
To proactively secure their environment, Interlace Labs quickly creates a violation policy that will be triggered whenever new instances are spun up in this particular virtual private cloud (VPC) and subnet. They can also brief Khon Traktour and explain everything that has occurred, educating Khon to ensure his continued application development is done in the most secure way. Leveraging the security incident as a learning opportunity helps avoid similar mistakes from being made in the future.
Lacework enables innovation without fear of attacks
The Interlace Labs breach story only scratches the surface of all the innovative capabilities Lacework delivers to its customers. Within the last year, Lacework has released agentless scanning, attack path analysis, active package detection, and CIEM capabilities. With the Lacework platform, Interlace Labs detected an active attack in its cloud environment and learned how the attack was carried out with aggregated composite alerts. With that data, it was easy to stop the attacker in their tracks.
Having confidence in your cloud security platform enables the business to constantly innovate without the fear of attacks. With the Lacework data-driven approach to cloud security, threats are easier to identify, regardless of the scale and complexity the cloud can create.
With confidence that known or unknown threats will be uncovered, security teams can leverage Lacework to prioritize cloud security risk with visibility and context helping them understand where to focus with reduced alert volume. These are game-changing benefits provided by a security platform that was built intentionally for the cloud. For a full Lacework demo of the Interlace Labs breach story, check out this video:
Suggested for you


