ESG Cloud Security Survey: Automation & Simplification are in
ESG Cloud Security Survey: Point products are out, automation and platform consolidation are in.
Source: ESG, a division of TechTarget, Trends in Cloud‐native Security Survey, January 2021
To secure applications in the cloud, the underlying infrastructure and orchestration layers like Kubernetes, digital businesses must confront new security challenges from both an architectural and organizational standpoint. New threat models must be addressed, while the roles of security and DevOps teams converge (known affectionately as DevSecOps), leading to what we like to call the “Shared Irresponsibility Model.” The old legacy approach to securing monoliths, from the technology to the security teams, simply does not work for the cloud.
ESG recently surveyed 383 IT and cybersecurity professionals in the US and Canada to find out how the shift to the cloud has continued to affect security among cloud-based businesses. The results are clear: the dynamic nature of cloud and containerized environments create pervasive blind spots, making securing cloud environments uniquely challenging, and DevSecOps program maturity gaps result in inconsistencies, misconfigurations, and lack of critical visibility.
A whopping 88% of all respondents believe that their cybersecurity program must evolve to protect their cloud native and public cloud workloads.
They need a consistent way to secure environments, and point products don’t deliver. Customers using modern infrastructure need a well-integrated, consolidated cloud security platform and must embrace DevSecOps as security has shifted all the way left into the product teams.
Major Takeaways From the Cloud Security Survey
Here are some of the survey’s greatest hits:
Point products are a pain, and they’re pricey.
Using multiple point products brings great cost and complexity, and leads to an inability to implement centralized policies. Security cannot work in silos when it spans teams, workloads, policies, and tooling. Customers need a unified, integrated, consolidated security platform.
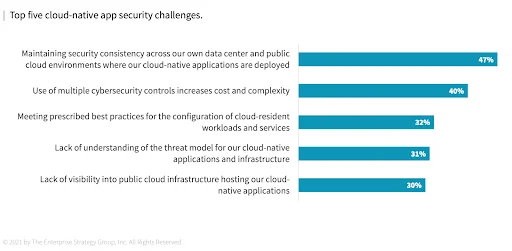
Figure 1: Top five cloud security challenges
74% report visibility blind spots making security monitoring challenges
If you can’t see it, and you can’t understand it, then you can’t fix it. Without access to the physical network and the dynamic nature of cloud-native applications and elastic infrastructure, the cloud security visibility gap is broad.
Anyone writing code has a critical role to play in the security posture of their workloads, and this makes misconfigurations easy to make and difficult to find. Effective cloud security posture monitoring can detect anomalies indicative of account takeovers resulting from Issues such as privileged cloud credentials, especially user credentials with administrative access to cloud, orchestration and service accounts.

Figure 2: Keys to improving security visibility for cloud-native apps
The most commonly reported types of cloud misconfigurations are simple human mistakes: poor IAM basics, such as the use of default passwords or lack of multi-factor authentication. Other threats include externally facing workloads subject to port scanning, overly permissive accounts targeted by bad actors, and unauthorized access to services. These misconfigurations end poorly, in data compromises as well as the introduction of malware, including crypto-miners and ransomware.
Additionally, the impact to SLAs indicates a need to automate updating infrastructure-as-code (IaC) templates via cloud security posture management (CSPM) controls.
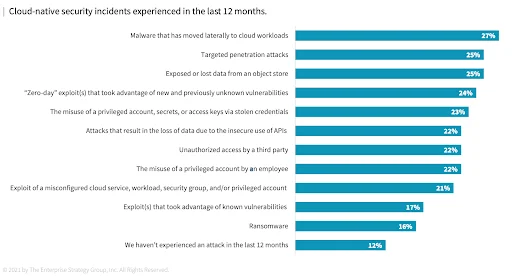
Figure 3: Cloud-native security incident data
41% say automating the introduction of controls and processes via integration with the software development lifecycle and CI/CD tools is a top priority
Cloud innovators are increasingly deploying their workloads using Infrastructure as Code (IaC), such as Terraform and Cloudformation, and they are also looking for ways to automate the deployment of their security tools seamlessly alongside their development teams’ CICD workflows.
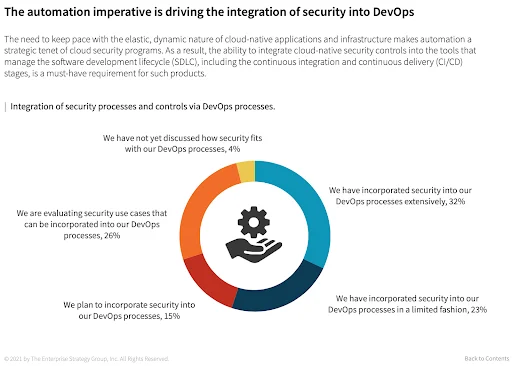
Figure 4: The automation imperative is driving the integration of security into DevOps
50% More than half of respondents indicated their organizations intend to consolidate to an integrated platform in the next 12-24 months
The consolidation to integrated cloud-native security platforms is underway
Cloud-based businesses need centralized control to the myriad services, workloads, configurations, APIs, and infrastructure underpinning their business. Integrated platforms enable a centralized approach to securing heterogeneous cloud-native applications deployed across distributed clouds, clusters, and teams. An integrated, single source of security truth ensures consistency across development and security teams for monitoring and securing applications and infrastructure.
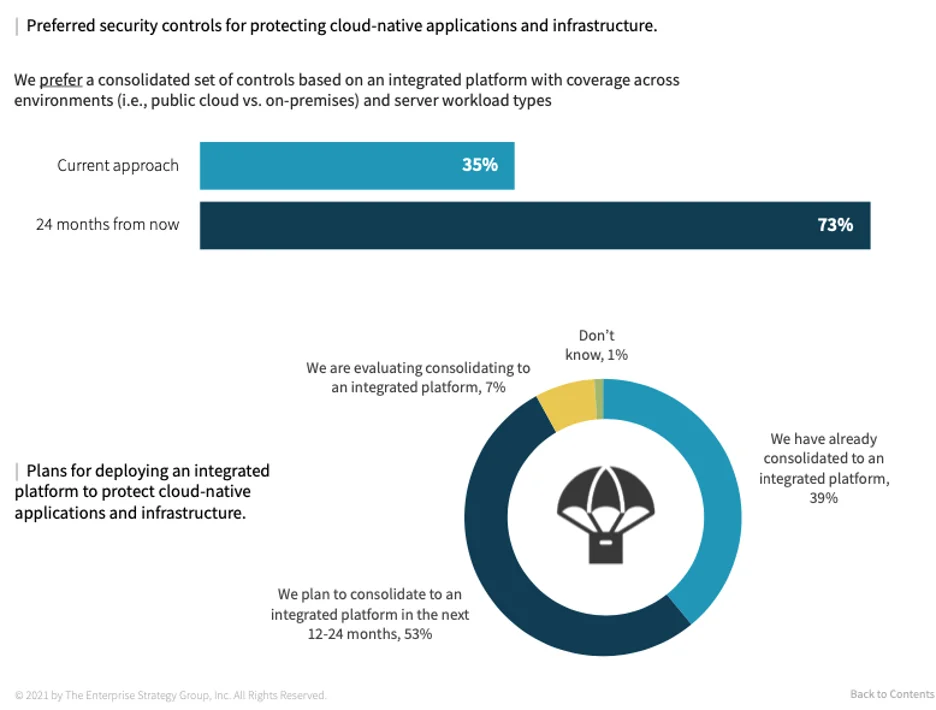
Figure 5: Preferred security controls for protecting cloud native applications and infrastructure
THE GOOD NEWS!
As DevSecOps use cases expand across the lifecycle, more cloud-native applications will be protected. Sometimes things get harder before they get easier, but the truth of the matter is that securing the cloud has the potential to be far much more scalable, more automated, more intelligent, and more comprehensive than ever before.
Secure DevOps best practices are finally beginning to be implemented across the application lifecycle, from the development stage to build and integration into delivery and production, which will result in an increase in those production cloud-native applications being protected via DevSecOps practices.
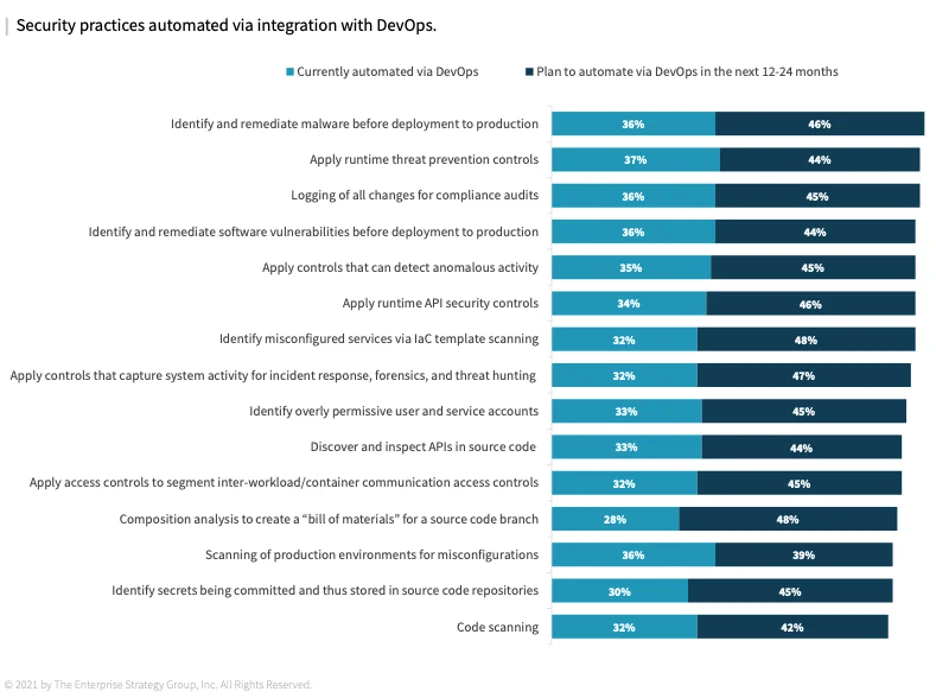
Figure 6: Security practices automated via integration with DevOps
Conclusion — Wrapping Things Up
In conclusion…The future is bright for cloud security. The vast majority of cloud-based digital leaders know that there is work to be done yet to ensure total protection of their cloud infrastructure and workloads, but by embracing the best practices and strategies laid out in the survey, they too can achieve DevSecOps serendipity.
To recap:
- Point products only bring more pain, more cost, and more complexity.
- Automation is required to scale security alongside cloud scale.
- Misconfigurations are common and insidious, but manageable with visibility and automation.
- Security must be embedded across the development lifecycle and integrated with CICD tools and workflows.
- A unified security platform is necessary in order to bring a centralized, common language to teams (DevOps and Security) and to integrate.
To view the complete survey results, access it here.
Categories
Suggested for you


