Detecting complex behavioral threats with AWS CloudTrail
Hopefully, you recently heard about composite alerts from Lacework, our latest innovation that detects complex and long-lived attack scenarios by stitching together patterns, tactics, and raw behavioral data from disparate sources such as AWS CloudTrail logs. In case you missed it, composite alerts are a game changer for Lacework customers because they efficiently and accurately enable users to find early signs of in-progress attacks that otherwise go unnoticed by SOC teams. In this blog, we will walk through how composite alerts work and the major advancements in security efficacy benefitting our customers and their security teams.
Most organizations we speak with are in the process of aligning their security strategy with Gartner’s cloud-native application protection platform (CNAPP). Gartner recommends implementing both posture assessment AND runtime breach detection capabilities.
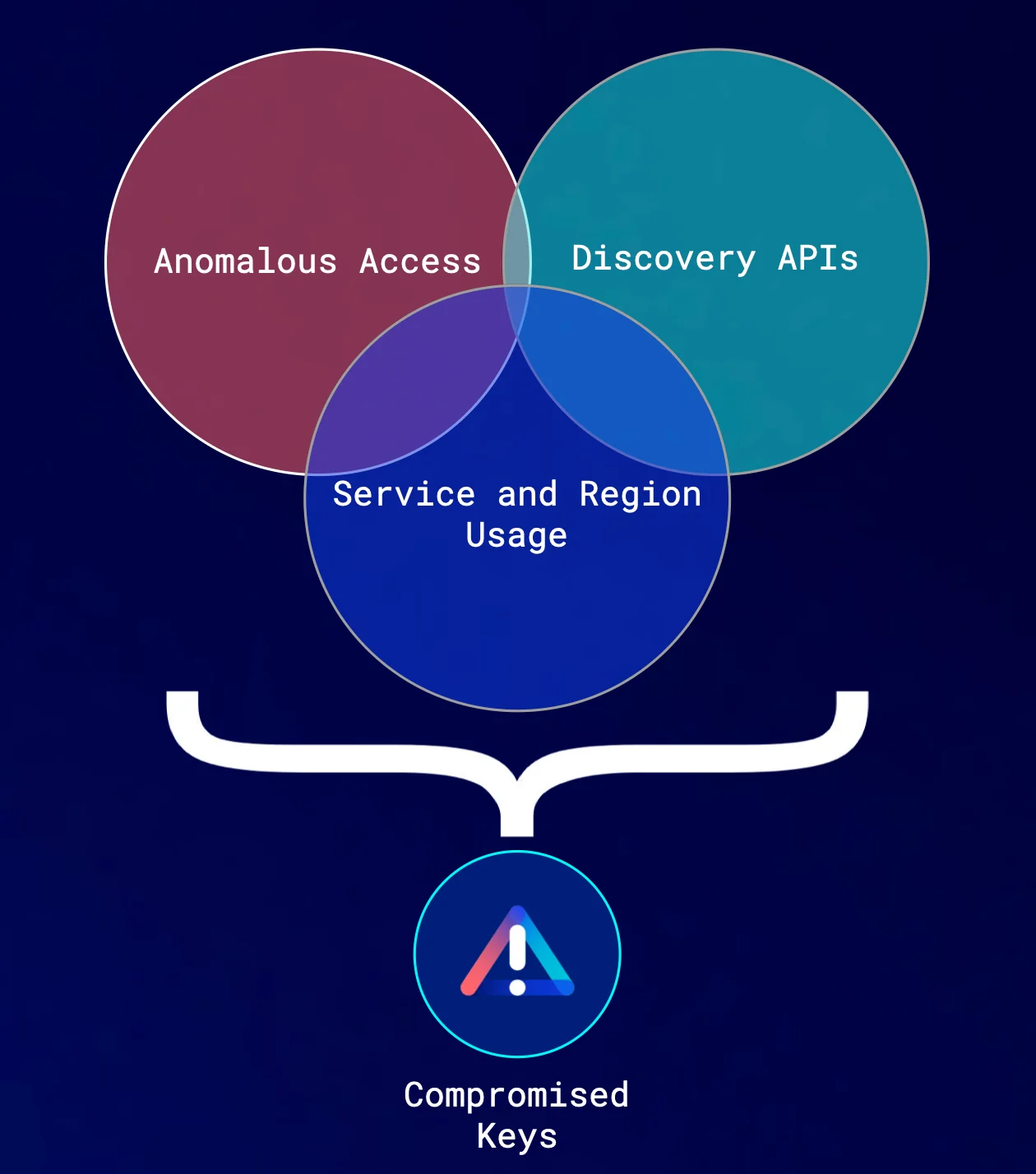
Our approach to detection is to treat any surface connected to the internet as vulnerable, and to use behavioral data to identify signs of malicious behavior. This means gathering network and process telemetry from servers and containers, and using data sources from control planes such as AWS CloudTrail or Kubernetes Audit Logs to look for important clues. Composite alerts are created using all of these datasets, automatically combining details, patterns, and tactics to identify complex exploits with very high efficacy and very low noise.
Subtle signals in every compromised IAM credential story
Composite alerts have multiple primary detection types. Let’s examine a specific scenario involving Amazon Web Services (AWS) Identity and Access Management (IAM) credentials being used by a malicious actor and how the Lacework Polygraph® Data Platform transforms raw AWS CloudTrail data into a collection of discrete and complex behavioral activities to deliver:
- A highly-confident event type, tailored for a specific complex scenario
- The scale and scope of the actions performed by the attacker during the incident
Breaking down the attack scenario:
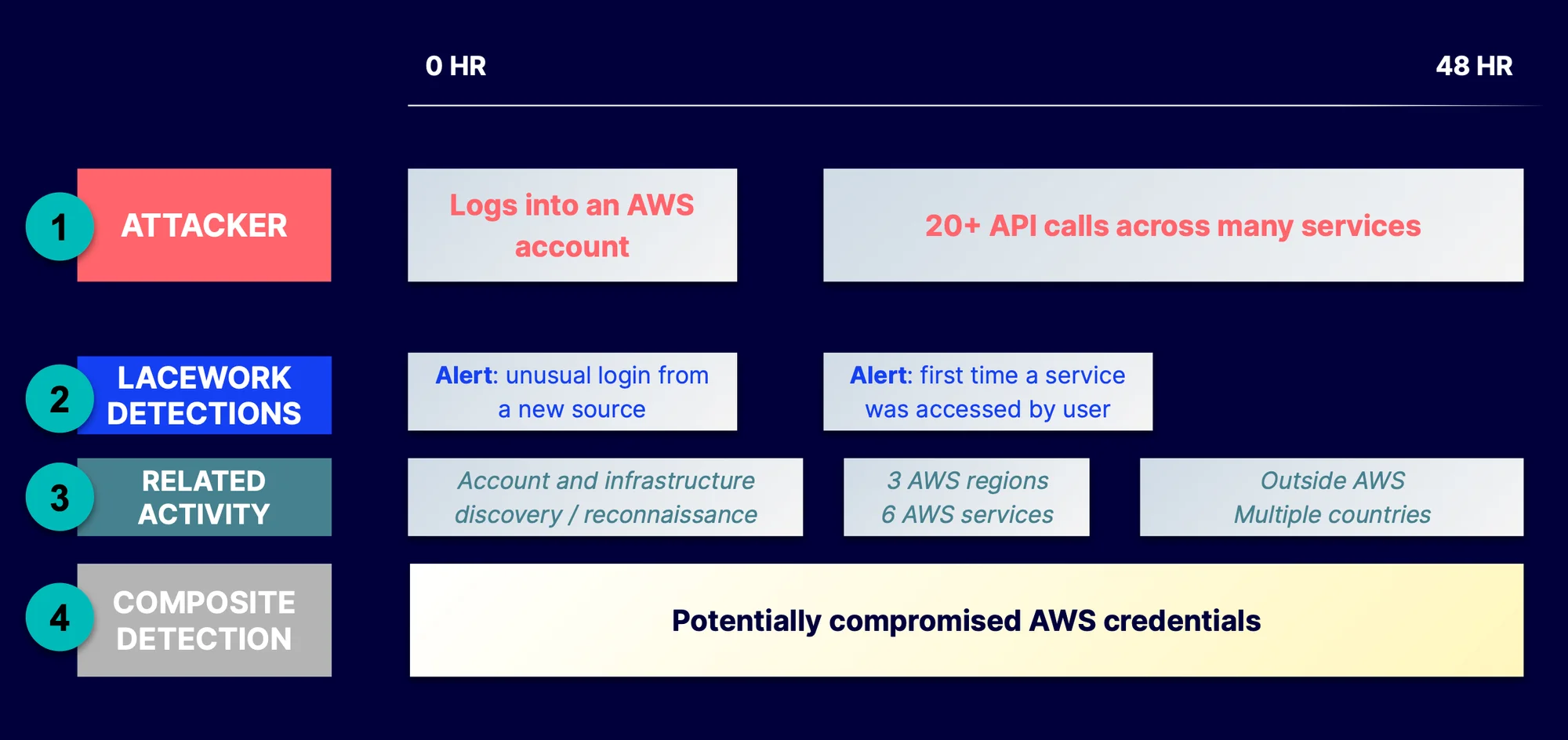
1. In the image, at the surface level, it appears that the attacker’s actions were relatively normal. They authenticated to AWS with the compromised credentials and interacted with some AWS services.
2. Even today, Lacework excels at detecting discrete, anomalous actions related to this event, and will surface these behaviors as suspicious activity for teams to investigate. These actions are referenced by the second row, in blue:
-
- Unusual login location: Lacework has not seen the user login from this geographic location before.
- First time a service was accessed: Lacework knows, historically, this user has never accessed this particular service before.
On their own, these actions are an effective signal that something suspicious has happened in your cloud environment.
3. With composite alerts, we use the above detections as a starting point to trigger a much deeper, automated investigation into the user’s activities. The scope is broad – both in time and criteria of what activities could be relevant. In particular, Lacework picks up on activity that would appear to be normal in most cases, if they weren’t otherwise associated with the anomalous activity. But together, they tell a different story.
4. This is critical to derive insights from CloudTrail activity – aside from login location or user agent, there isn’t much else that signals malicious activity. Deep inspection of user activity, combined with anomalous behavior detection, is the only consistently reliable way to separate normal activity from bad.
A composite alert policy, such as “Compromised AWS Credentials,” is designed to spot combinations of both anomalous behaviors and specific actions that are commonly seen together in an attack scenario. An example may be:
Logging in from a new location + API calls indicating reconnaissance
When enough of these conditions are met, a high-confidence alert will be generated with contextual investigative detail automatically embedded in the alert.
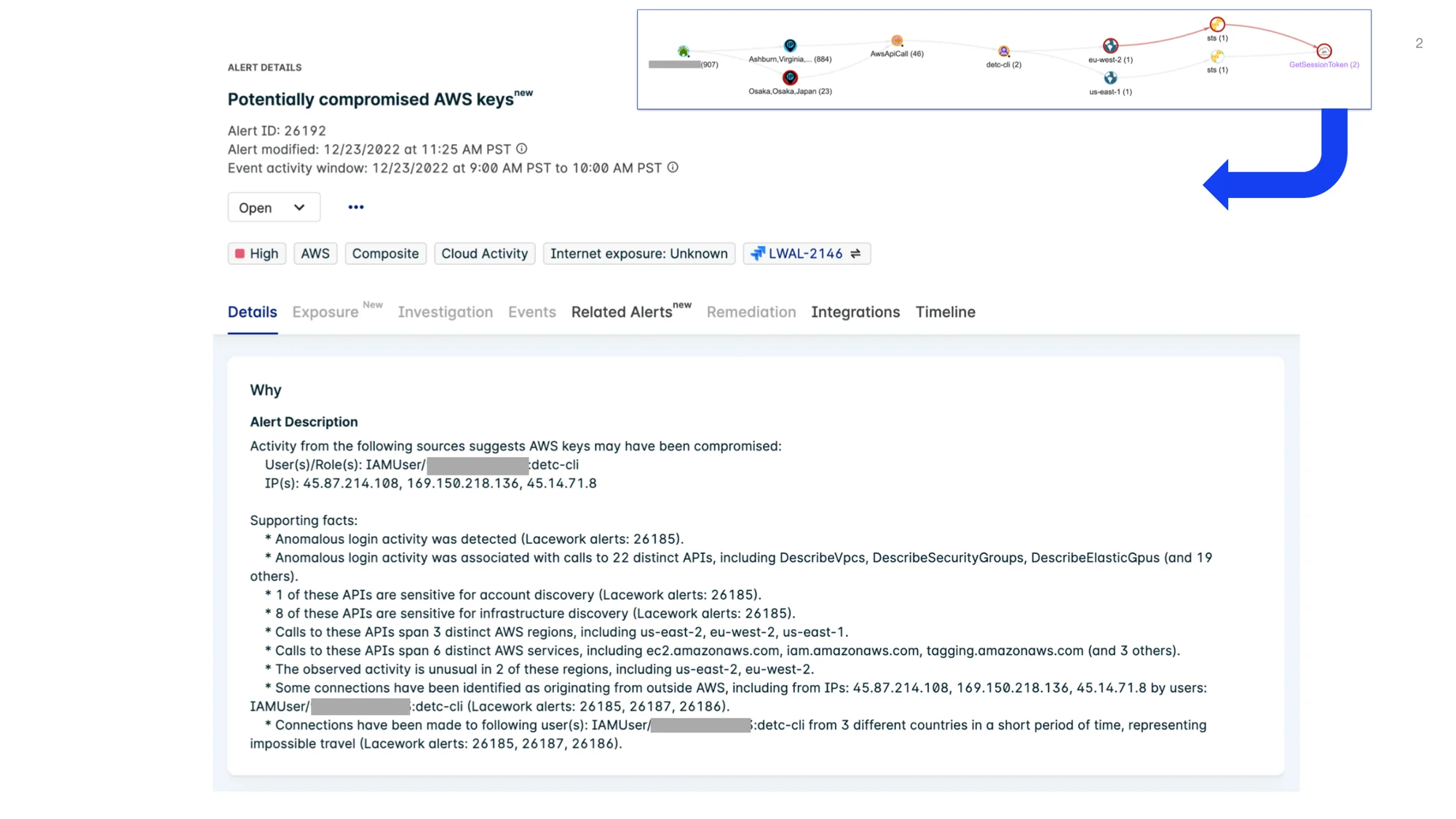
Actionable, detailed alerts
Detection is only half of the story. The same engine that is computing behavior, collecting evidence, and deciding whether to raise a signal, is also able to aggregate this evidence into a series of supporting facts for use by the incident responder.
In this example alert, you can see the supporting facts include quantifiable information such as the scale and scope of how many regions, services, and APIs were interacted with.
By reducing investigation time of a real incident (on average, less than 5 minutes of investigation before moving to incident response), we can significantly impact mean time to respond (MTTR). This directly reduces the window of potential impact by an attacker.
When we reduce MTTR across all events and reduce false positive rates, we can significantly decrease the load on security and SOC teams at scale.
A generational leap in detections and automated investigations
Lacework does a great job of narrowing down critical or high alerts based on behavioral analytics and anomaly detection. Composite alerts go beyond alerting on individual data points. They further reduce false positives and investigation times, while improving efficacy by transforming subtle but suspicious events into high-confidence complex breach incidents.
Because AWS CloudTrail data contains all actions performed by all authenticated users, identification of the attackers becomes more difficult. When credentials are compromised, organizations need clear, confident signaling with immediate scoping and scaling details.
AWS CloudTrail is an essential part of maintaining security in your AWS cloud because it provides visibility into your account activity across your AWS infrastructure. With AWS CloudTrail, you have the ability to view, search, download, archive, analyze, and respond to account activity and with details that help in responding to malicious activity in your AWS account.
So why does this matter to you?
By combining the insights from AWS CloudTrail with the innovation of Lacework composite alerts, you have the ability to gain early detection of malicious attacks in progress that could otherwise go unnoticed. Our platform correlates, on average, seven to eight low severity alerts for each composite alert policy, drastically reducing investigation times and false positive rates – saving you time and energy uncovering what all this data really means to your organization. As a consumer of AWS CloudTrail and Lacework, you now have unparalleled insight into your cloud environment activity, unlike ever before. At Lacework, we are constantly innovating to help our customers see novel detections and tactics beyond the MITRE attack framework. Composite alerts will be our way forward!
Additional AWS CloudTrail-driven composite alerts available at this time (May 2023) include :
- Compromised credential attack
- Potential AWS defense evasion
- Cloud ransomware
- Cloud-based cryptomining
To learn more about our AWS CloudTrail integration, check out our latest integration brief.
Suggested for you