Finally, a reason for your developers to want an agent
Nearly everyone can name a highway where the road work seems to never end.
I lived in east Tennessee for 12 years. And, living in east Tennessee, I became intimately familiar with Interstate 40 — the long road that stretches from Barstow, California to beautiful Wilmington, North Carolina.
For all 12 years, there was a stretch of I-40 where the road work never ceased. Seemingly every day, the area was packed to the brim with road workers. And the work was warranted. This was an area where I-40 merged with two or three other highways, creating a complicated overpass. No matter how many lanes the workers closed, the cars kept coming. High traffic, high impact.
Now, imagine that the same group of road workers was diverted mid-project from high impact I-40 work to do bridge repairs on a rural country road. They repair that bridge for months, exercising their craft. After all, the bridge technically does need to be repaired. It has obvious flaws. But after they finish the job, they find out that the country road is rarely used. In fact, it hasn’t been used for several years. And, while their attention has been on this isolated bridge, the condition of the half-finished, high traffic I-40 project has slowly deteriorated until, now, it’s a real danger to the public.
But that would never happen, right? Public officials would direct time and money toward the projects that would deliver the best ROI. It would be ludicrous to shift limited resources away from the highest impact projects toward something that’s likely not even going to move the needle.
So why do we do this with cloud security?
Dealing with the never-ending to-do list
The answer is simple: because you don’t know what you don’t know.
For years, cloud security has been a game of whack-a-mole. Cloud data is interconnected and is constantly moving and changing. And even the slightest movement or change can trigger a security risk. Which triggers an alert. Before you know it, you have a bunch of flashing red lights, and teams are left running around, “whacking” as many of these lights as possible.
But, here’s the problem. Some of those alerts are bridges on country roads — fixes that lead to a dead end. And at least one or two of those alerts are I-40 repairs. So how do you know which is which?
It is impossible to respond to every single vulnerability. At last count, the U.S. government’s National Vulnerability Database (NVD) is reporting a whopping 200,000+ vulnerabilities, 18,000 of which are listed as critical and 50,000 of which are listed as high severity. Mind boggling numbers.
At last count, the U.S. government’s NVD is reporting a whopping 200,000+ vulnerabilities, 18,000 of which are listed as critical and 50,000 of which are listed as high severity.
So how can security teams determine which “critical” risks are non-negotiable fixes and which can be placed on the backburner? And how can these security teams, then, spare developers from sinking precious time into fixes that aren’t going to reduce risk?
Active vulnerability detection helps reduce 90% of critical vulnerability noise
Lacework recently announced a series of platform enhancements that will drastically improve vulnerability risk management for security teams. The apex of these features is a new, custom risk-based vulnerability scoring mechanism, where each vulnerability inside a customer’s cloud environment receives a score, based on factors unique to their environment. To create this score, we take NVD critical vulnerabilities, then layer on unique customer attributes, including which ones may be exposed to the internet, what critical data assets are in the vulnerability’s path, and whether active exploits exist in the wild.
As a part of this risk score “cocktail,” we also use our lightweight agent to determine whether vulnerable software packages are active in production — something we’re calling active vulnerability detection. Remember that never-traveled country road? Active vulnerability detection makes sure that your developers never work on those dead ends and that you’re only dedicating your attention to work that matters to you.
Active vulnerability detection makes sure that your developers never work on those dead ends and that you’re only dedicating your attention to work that matters to you.
This feature solves the problem of prioritizing alerts and reducing false positives that are associated with software bloat, where developers package more software than is needed for an application to operate. Lacework eradicates this issue by ensuring that only software that poses an active security risk is upgraded.
Lacework continuously and completely monitors the file system of any and every host in the cloud at all times. This means that when a package is executed, the agent detects this activity automatically. This information is then quickly reflected in our new customized risk score and the Lacework console. By combining active vulnerability detection, attack path analysis, proprietary research from Lacework Labs, and commercially curated exploit feeds, Lacework is able to help customers reduce critical vulnerability noise and work more efficiently.
Based on early customer results, this new customized risk score can allow you to safely reduce your critical vulnerability noise by up to 90%. Suddenly, that to-do list that looked unmanageable is whittled down to something more feasible.
This feature will bring smiles and whoops of delight from your developers who can now spend significantly less time on security and focus on building value for the business. They will also appreciate the high level of actionable guidance you provide to help them resolve issues quickly. Three cheers for increased productivity, happier employees, and bolstered trust between security and development teams.
And maybe, now, you’ll have an easier job selling your runtime agent to your development teams.
How does active vulnerability detection work?
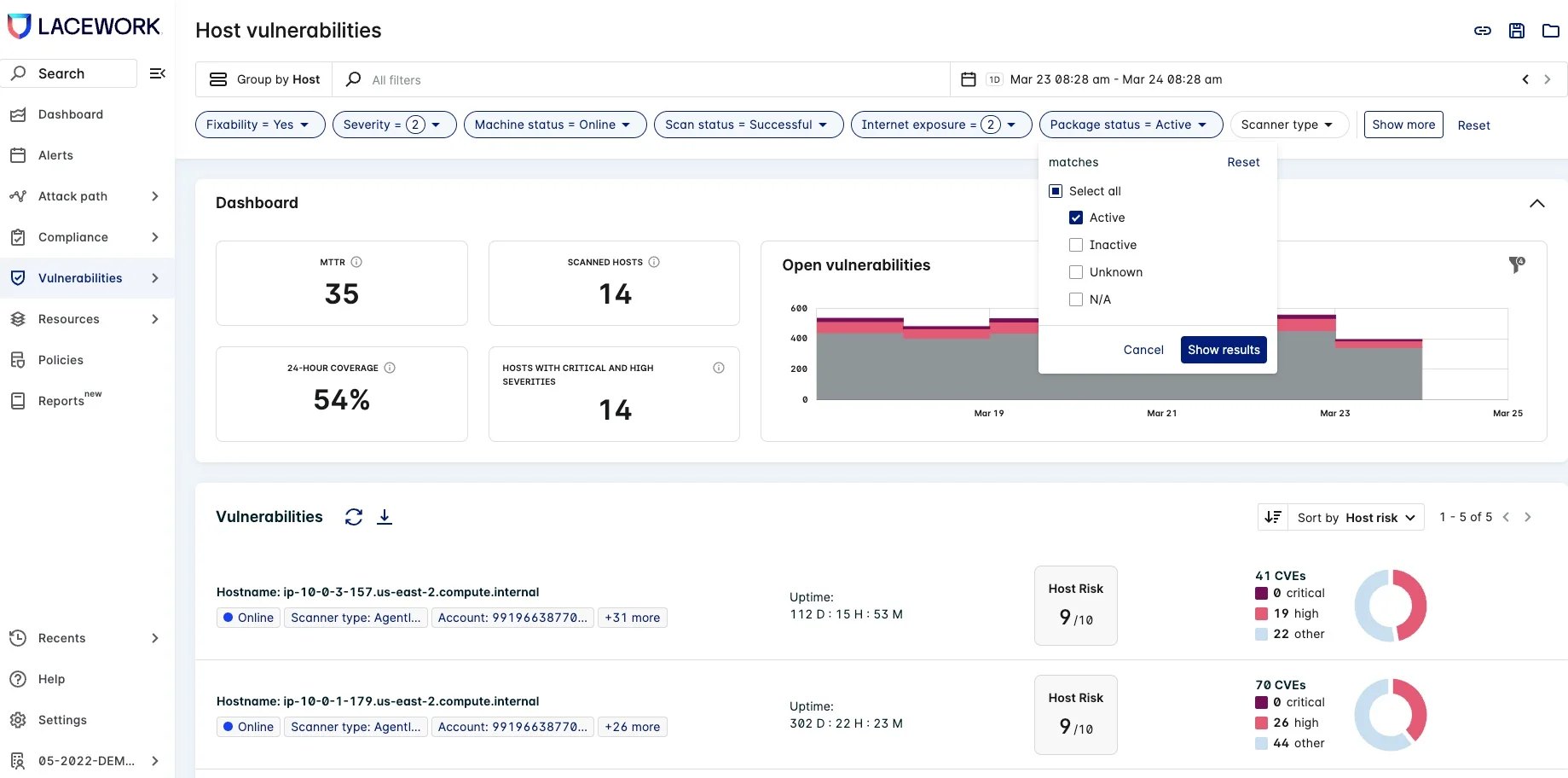
Incorporating this valuable feature requires no additional lift from users — it is on by default. From the user interface, using the new “Active images” view found within the Vulnerabilities tab, security teams can see only the vulnerabilities within active packages. Are you worried about performance impacts? Don’t be. Active vulnerability detection has negligible impact on CPU, memory, or data volumes.
Figure 1: Active images view found within the Vulnerabilities tab
What a true CNAPP looks like
Back in 2021 when Gartner coined the term “cloud-native application protection platform” (or “CNAPP”), the firm’s vision was for a single unified cloud security platform whose nature reflected that of the cloud itself — integrated and seamless. A single place to meet all cloud security needs across the entire cloud-native application lifecycle by connecting data across parts of the cloud that would have traditionally been siloed.
But what have we gotten since then? Point solutions that only solve half of the puzzle, yet call themselves “CNAPP.” Collections of poorly integrated products under the “unified platform” banner. “Solutions” that make security teams’ jobs incrementally better, at best.
So what does a real CNAPP look like? Honestly, it looks a little bit like active vulnerability detection. Here’s how:
As the cloud attack surface continues to grow, organizations must be able to secure their environment by correlating information about risks and threats from a single, scalable platform. With active vulnerability detection, Lacework makes the lives of your security and developer teams exponentially easier by actually tying together vulnerability data from across a cloud environment to contextualize and ultimately identify active vs. inactive packages.
That’s right. A single platform covering both build time and runtime that automatically correlates data that would have historically been isolated. Lacework is not simply a collection of cloud security functions — CSPM, CWPP, IaC, vulnerability management — all under the same roof. It’s all of those functions feeding into each other. It’s one symbiotic cloud security organism. It’s CNAPP.
Lacework is not a simply a collection of cloud security functions — CSPM, CWPP, IaC, vulnerability management — all under the same roof. It’s all of those functions feeding into each other. It’s one symbiotic cloud security organism. It’s CNAPP.
And active vulnerability detection is just one way Lacework is delivering on the promise of CNAPP. Check out our recent attack path analysis updates for more CNAPP innovations.
From the beginning, Lacework has always supported a defense-in-depth approach to cloud security. Lacework provides agentless ways to quickly detect misconfigurations, vulnerabilities, and threats in your cloud accounts, while also offering an agent-based approach that continuously monitors your applications and workloads for active threats and, now, for critical vulnerabilities that truly matter.
Modern cloud environments require this type of holistic security approach with a breadth of coverage that provides security for your many different accounts, services, and workload layers. Only this combination of capabilities can help you get secure – and stay secure.
–
Alright, back to road work. In Robert Frost’s famous poem The Road Less Traveled, the traveler at the fork decides to take the often neglected road. A good lesson in life — often, the wiser decision is to follow the unknown path that features the least amount of footprints.
However, when it comes to cloud security, we can’t afford to make that decision. Find your I-40 and fix the highest impact issues with the most at stake. And that will make all the difference.
Check out this page for additional information on how the Lacework CNAPP helps you prioritize cloud security risks faster than ever before.
Suggested for you