Find big threats in small signals with new composite alerts

In 1943, British board game designer Anthony E. Pratt created a game that would end up becoming a global phenomenon. The premise of the game is simple — use logic to solve a murder. You may be familiar with this game, known to many as Clue.
In Clue, the items of the crime are innocuous on the surface. A candlestick. A wrench. A knife. A cast of characters like Colonel Mustard and Professor Plum. A ballroom. A library. On their own, none of these pieces are significant. But, like any crime scene drama, these insignificant pieces can be stitched together to reveal something of great importance.
In many ways, cloud security is similar — seemingly benign alerts can, when tied together, point to real risks and threats. However, in isolation, these alerts can get buried underneath a pile of singular, higher priority items. Scoring security events in isolation makes it difficult to know what to fix first. And querying through the alerts and manually connecting evidence like yarn on a bulletin board is simply not possible at cloud scale.
But some good news? It’s possible with automation. And now, it’s possible with Lacework.
Lacework introduces composite alerts
Today, Lacework is releasing new capabilities into its industry-leading cloud native application protection platform (CNAPP). Through the composite alerts feature, our platform will detect active cloud attacks by automatically correlating, on average, seven to eight low severity, seemingly disparate security events that otherwise go unnoticed by security teams into a single alert.
Now businesses can more easily identify attacks in progress — such as cloud ransomware, cryptomining, and compromised credentials — with a high level of confidence, and without excessive querying, or significant expertise, effort, or time.
Typically, security analysts or incident responders detect or investigate threats by aggregating and analyzing data through a security information and event management (SIEM) solution. However, this often requires someone to write and execute a large number of individual queries to first identify each event and then discern what is happening in their environment.
With Lacework, there is no need for customers to set manual rules or configure anything. Lacework automatically correlates and analyzes all events in totality to help security teams quickly investigate potential attacker activity, thereby saving time and costs.
Lacework is the first CNAPP vendor to use this type of automated, platform approach to look for early signs of active attack patterns and tactics, delivering a high-confidence composite alert when it suspects a specific type of attack for greater security efficacy and efficiency.
Too many alerts, too little time
The cloud, for all of its benefits, comes with one major shortcoming: it offers a much larger attack surface. With the growing prevalence of cloud-based attacks, it’s understandable why security teams don’t want to dismiss an alert as a false positive and often worry about the business impact of false negatives. However, strained security teams are forced to spend the bulk of their time investigating their most pressing issues and can’t dig into the lower severity alerts.
But in reality, real threats may be hiding in these medium, low, or informational alerts. Today’s cybercriminals are constantly evolving their techniques to fly under the radar and avoid detection for as long as possible. They know the security controls that trigger high or critical alerts and, therefore, use evasion techniques to prevent such notifications — especially when they are doing reconnaissance in the early stages of an attack.
Now, with the composite alerts feature, organizations can be more confident than ever that they are detecting critical and high severity alerts, while not missing real threats like ransomware, cryptomining, or compromised cloud credentials, even as these exploits try their best to hide.
How does it work?
Unlike individual events, a composite alert continuously monitors and detects unusual activities and malicious patterns over a period of time. Our platform then automatically determines what events and behaviors are relevant and stitches them together to determine if they match any known attack patterns.
Let’s look at this example: an attacker compromises your Amazon Web Services (AWS) credentials. You can also walk through this example in our interactive demo.
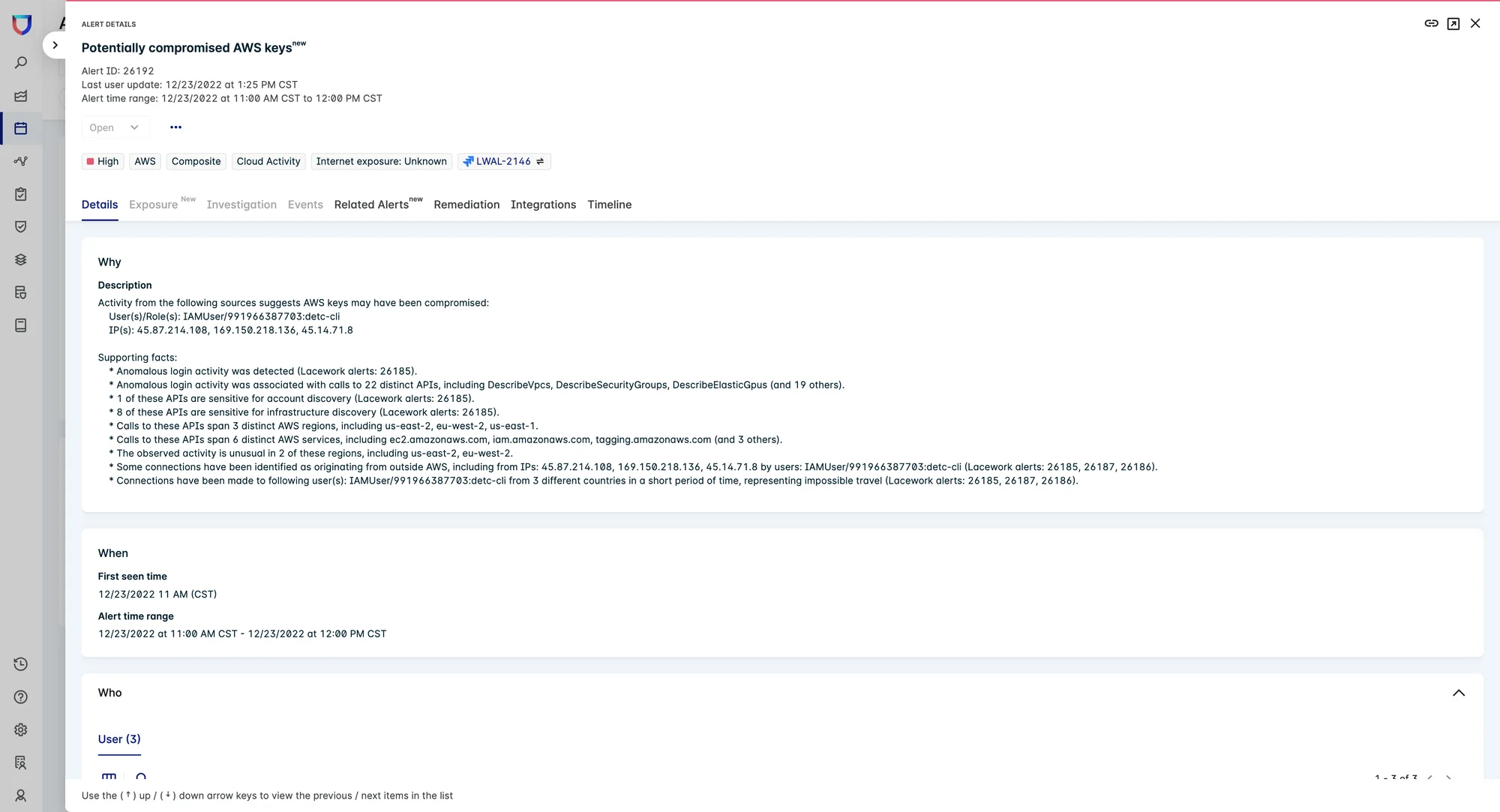
First, an attacker logs into an AWS account. Lacework generates a single alert, as it is an unusual login originating from a new source in Japan. Typically, once an attacker authenticates into the environment, they begin systematically probing the environment for the purposes of discovery and information gathering. Attackers start by finding weak spots in an organization’s defenses and controls, and then attempt privilege escalation and lateral movement to gain access to sensitive data or systems.
With AWS, these enumeration activities are achieved by interfacing with various APIs. In this example, Lacework leverages CloudTrail logs to determine that the anomalous login was associated with multiple API calls, some of which are related to sensitive account and infrastructure discovery activities. This also reveals that the API activity spanned three different AWS regions and AWS services, some of which were accessed for the first time.
Finally, Lacework determines that some of the connections originated outside of the AWS, with connections made to a particular user from three different countries in a short span of time, indicating impossible travel.
Normally, the victim organization would receive multiple alerts for this scenario — for anomalous login, suspicious use of a new service, new region, or new connections. With Lacework, users receive a single, high-confidence composite alert with all the context needed to effectively triage and investigate.
Learn more about composite alerts
With the cloud, new events happen all the time. And Lacework does the detective work for you. Our platform makes it easy for organizations to quickly detect specific threats such as AWS credential compromises and cloud ransomware attacks by automatically correlating individual events across disparate sources and providing all the context and supporting evidence in one alert.
So, no, the misdeeds aren’t happening in the conservatory or the kitchen. No Miss Scarlet. No Professor Plum. We’ve traded candlesticks for API calls and wrenches for IP addresses. There are obvious differences between Clue and cloud security. But, in a way, the objective is the same: uncover bad actors as fast as possible.
Check out our 2-minute feature tour video or our interactive demo to learn more about how composite alerts can help your team speed investigations and mitigate risks at scale.
Suggested for you