It’s time to scale up your cloud security posture
By: Ginnie Goodman, Product Marketing Manager

Organizations need better visibility into their cloud security posture so they can better understand and manage their risk and achieve compliance. But operationalizing posture at scale can be daunting and resource intensive.
This is why Lacework has been focused on continually delivering the deepest visibility and multicloud security posture assurance for our customers. Today, Lacework is releasing new cloud security posture management (CSPM) capabilities to help organizations achieve operational excellence and effectively manage security and compliance at scale, all from one flexible platform.
This enhanced CSPM feature set is generally available for Amazon Web Services (AWS), Google Cloud, and Microsoft Azure and allows organizations to:
- Create fine-grained custom policies to ensure configurations align with your specific needs
- Build custom cross-account reports to measure hygiene
- Achieve operational excellence with the latest CIS benchmarks, industry standards, and hundreds of other additional controls written by the Lacework Labs team
Building posture is hard; maintaining posture is harder
Misconfigurations are a leading cause of cloud breaches. According to the IBM Cost of a Data Breach Report 2022, misconfigured clouds cost organizations an average of $4.14M annually.
The problem is, it’s easy for misconfigurations to happen, largely because obtaining full visibility into cloud resources is a huge challenge. The dynamic nature of the cloud makes it difficult to quickly identify and remediate gaps stemming from resource changes.
As a result, organizations have turned to CSPM to solve these issues — and have found some success. However, larger organizations or those with a significant cloud footprint still find maintaining and operationalizing cloud security posture at scale to be a unique challenge. Current approaches often require excessive internal resources for management, but they often lack sufficient flexibility, and cannot scale across multiple cloud providers.
Carve out your own posture
No two clouds are the same. And the nuances of an organization’s infrastructure often dictate very specific regulatory and business requirements that are often not covered in standard benchmarks. For this reason customization is essential to designing a cloud operating model that addresses your diverse use cases and needs.
With Lacework, you can now easily create custom policies for AWS, Google Cloud, and Azure to secure your cloud infrastructure, enforce your own set of business standards, and monitor for any compliance violations. You can also design and run fine-grained security assessments that automatically keep up with your cloud’s IT operating model and go beyond standard benchmarks.
How does it work?
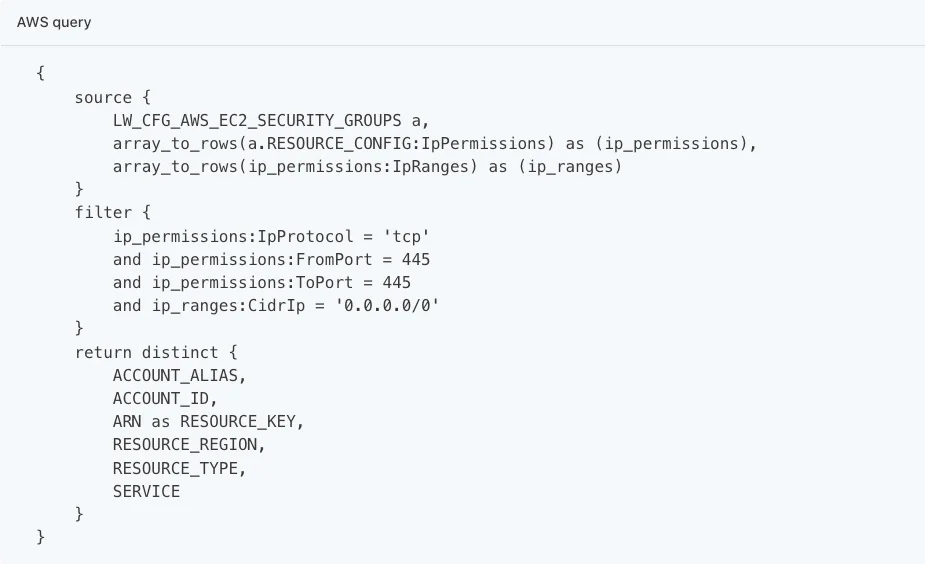
We support custom policy creation for AWS, Google Cloud, and Azure resources using Lacework query language (LQL), allowing you to validate the compliance of cloud resources against your own internal checks.
Say, for example, you want to create a policy for when a storage bucket or database is publicly accessible. First, define the conditions and allowed behavior. Using LQL, you can query, set status alerts for specific cloud configurations, and receive an alert — on a per resource basis — each time a resource fails against a particular policy. The alert will indicate which discrete cloud resource is non-compliant with a specific custom policy.
You could choose to be notified when a configuration scan detects a user-defined resource configuration policy violation that could undermine or diminish your risk posture. You could also choose to receive an aggregate alert when there is more than one resource affected by this violation. Finally, you can choose your alert channels. Any changes in compliance status of custom policies can be quickly escalated with alert integration into Slack, Jira, ServiceNow, etc.
Generate custom reports to measure hygiene
For even more flexibility, organizations can now build custom cross-account CSPM reports to meet the specific needs of different stakeholders, auditors, and customers.
These tailored reports can reduce the hassle of manual evidence gathering by automatically compiling findings for multiple purposes and audiences. They can also help you scale by automatically generating custom reports for the checks that are most important to your organization.
To build custom reports, you select the controls (policies) that run and choose your preferred intervals and severities. You can then specify the preferred policies you’d like included in the report and the order in which they are displayed. You can also schedule how often the reports will be run and who will receive them via email.
Gain more controls to assess your cloud security posture
We do, however, realize that custom policies may not be for everyone. To that end, Lacework features hundreds of pre-built policies that customers can use to maintain a solid cloud security posture.
To ensure your cloud follows the most recent security recommendations, Lacework policies and reports have been updated with the latest benchmarks: CIS 1.4 for AWS, CIS 1.5 for Azure, and CIS 1.3 for Google Cloud, now generally available and all mapped out-of-the-box against multiple industry benchmarks (SOC2, PCI-DSS, ISO 27001:2022, NIST, etc).
Our CIS benchmarks are ready to use and don’t require any special configurations. These updated policies offer increased accuracy and comprehensive security checks, so that you can identify risk and compliance violations more readily. You’ll gain immediate, actionable insights for firm cloud security posture, with easy to understand findings, and compliance summaries that include details on severity levels and remediation guidance.
In addition, based on our expertise helping AWS customers secure their cloud, we provide over 100 additional policy checks that lend stricter controls for S3, IAM, and VPC policies, including resources on AWS GovCloud.
To accelerate your ability to remediate and make CSPM even more actionable, Lacework also offers IaC scanning. Our IaC security functionality helps organizations uncover misconfigurations at the earliest stage of development and prevent costly mistakes in production.
Next steps
Over 75 percent of Lacework customers identified CSPM functionality as their top driver in choosing our platform. To learn more about how you can validate your security and compliance posture from a single platform, check out our solution brief or this interactive demo
Categories
Suggested for you