Malware targeting latest F5 vulnerability
Chris Hall and Jared Stroud - Cloud Security Researchers, Lacework

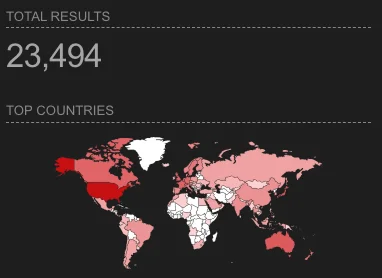
Public-Facing BIG-IP Appliances
Hunting for Malware
Lacework Labs has identified from their honeypot data CVE-2022-1388 being exploited. Post-execution activity ranges from simply executing “id”, to downloading and executing a second-stage payload. From this data, Lacework Labs developed YARA rules to hunt for the unique URI targeted in the F5 vulnerability and associated ELF files. This resulted in numerous hits for Miria variants for various architectures demonstrating how quickly malware authors can adopt PoCs to distribute their malware. When analyzing the executable capabilities for exploiting other vulnerabilities aside from CVE-2022-1388 were discovered to include Log4J, ColdFusion, and various home router exploits. An example of this can be seen in the Ghidra pseudocode below highlighting a payload to take advantage of CVE-2022-1388.
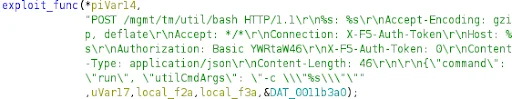
Figure 1 – Example CVE-2022-1388 exploit template
Further examining the binary, a section of code with numerous XOR encoded strings were identified. Given that the Mirai source code was leaked years ago, cross-referencing the available source code gives further insight into changes an individual threat actor may have made for their Mirai variant. The code snippet below shows the entries discovered within the sample we analyzed on the left, and on the right shows the publicly available source code.
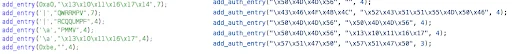
Figure 2 – Mirai source vs decompilation
The “add_entry” function contains a decoding routine that leverages a single key of “0x22”. This allows us to easily decode said strings as shown in Figure 3. These strings are then used as credentials for brute force activity.
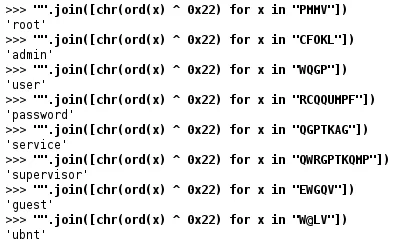
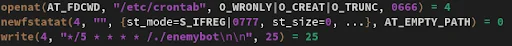
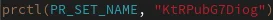
When executing, a crontab (T1053.003) entry is set to execute the binary every five minutes. Finally, during execution prctl is leveraged to rename the executing binary to a random set of characters before continuing brute force efforts.
Identifying Researchers
Along with exploitation in the wild using Mirai, Lacework Labs also observed activity originating from Project Discovery. Project Discovery maintains a repo for a popular open source scanner dubbed Nuclei which is used for both traditional scanning and recon as well as more invasive tests using OAST. To enable scanning the Nuclei community curates configs for various exploits. The configuration for CVE-2022-1388 was committed to Project Discovery’s GitHub on May, 9th and Lacework has seen a moderate amount of related traffic from varied sources. For more info on Project discovery check out our recent blog here.
Categories
Suggested for you


