Lacework enhances threat detection with data-driven, ML-enhanced capabilities
Why did the ML model break up with the cloud? The model couldn’t handle its altitude.
Navigating the complexity of cloud security
In ever-expanding cloud environments, security teams grapple with a significant challenge: discerning regular or “normal” activities from those that are risky or suspicious. The dynamic nature of these environments often leaves teams unsure of where to direct focus. This uncertainty, coupled with the responsibility of protecting the business, demands a solution that not only detects threats but enables security teams to effectively respond.
Embracing data as the cornerstone of security
At the core of our philosophy at Lacework is the understanding that effective security is fundamentally a data challenge. Cloud-generated data — a vast resource — has largely remained untapped in the realm of threat detection and response. Recognizing this, Lacework has adopted a unique approach to harnessing this data, transforming it into a powerful tool for identifying and managing security threats using a private by design approach which protects the confidentiality and privacy of customer data.
Lacework continuously invests in refining the mechanisms of data capture and analysis within cloud environments. The platform’s approach offers advanced anomaly detection that does not solely rely on predefined rules. Lacework establishes an activity baseline by creating a comprehensive view of cloud workloads, API interactions, and cloud-based activities, all in a privacy-preserving manner. This baseline serves as a comparison point, enabling the system to identify deviations that may signal potential threats.
The journey doesn’t end with data capture and analysis. Lacework is pushing boundaries with further integration of technologies like Artificial Intelligence (AI) and Machine Learning (ML). These technologies are pivotal in augmenting the platform’s capability to detect an expanded range of threats at earlier stages in the attack lifecycle. This proactive approach not only enhances security but also positions Lacework customers ahead of potential breaches and corresponding business impact.
Latest updates to Lacework threat detection and alerts
This month, Lacework is releasing several updates to its threat detection and alerting capabilities:
1. New AI/ML models for threat detection
Lacework has implemented three new machine learning models to monitor for emerging threats and attacks:
- A Domain Generation Algorithms (DGA) model to detect malware infections or compromised hosts. This model recognizes patterns used by malware in command and control communication channels, based on MITRE ATT&CK T1568.002. The model goes further than the traditional approach, eliminating false positives by incorporating a historical baseline of domain activity for each customer.
- An SSH brute force model to identify unusual patterns of login attempts, based on MITRE ATT&CK T1110.001. This model is useful for detecting follow-on activity once an attacker has access inside of a cloud environment.
- An active scanning model designed to detect a substantial number of outbound port or IP scans, based on MITRE ATT&CK T1595. Most detection mechanisms look for internal scanning, this model is different and looks for attackers probing internal infrastructure for reconnaissance purposes.
Combined, these new models bolster the effectiveness of Lacework alerts by broadening the detection areas, and enabling earlier notification of potential attacks.
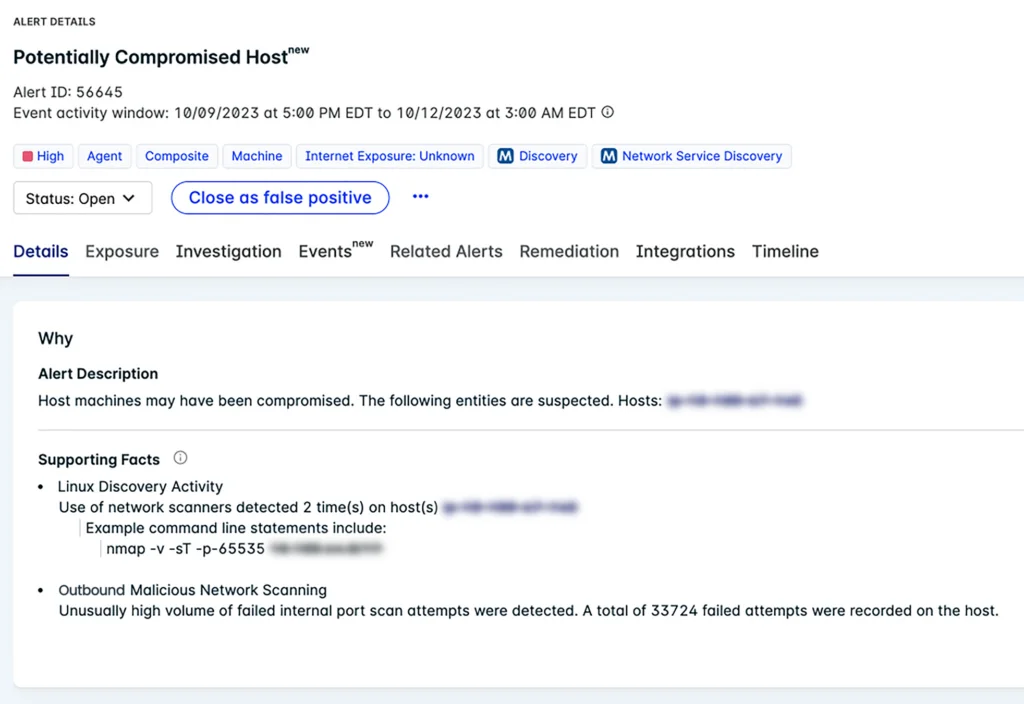
Figure 1: Lacework Composite Alert illustrating a compromised host
2. Introducing risk analytics for more effective threat detection
Recently launched features help Lacework customers understand the nature and severity of detected threats. At the heart of the innovation is the strategic use of environmental data to create customized threat assessments for detected activities. By analyzing the distinct patterns and behaviors unique to each client’s environment, the platform’s data-driven approach distinguishes between normal, routine cloud operations and genuine threats, enhancing detection and alert accuracy like never before.
A groundbreaking addition to the Lacework detection arsenal is a new risk analytics tool. This tool sets a cross-customer baseline by analyzing activities across multiple anonymized customer environments. It offers users a panoramic view and highlights how peer environments are operating and responding to threats or benign activities. For example, if a significant number of peers are responding to compromised hosts or containers, this tool signals the critical need for similar actions, amplifying the urgency and importance of prompt responses. Conversely, the tool also plays a role in identifying commonalities across customer environments. Lacework will adjust the severity of alerts to account for benign or common activities, reevaluating the environment to accurately reflect the risk. By harnessing this power of collective insight and intelligent risk assessment, we are empowering users to make more informed, effective decisions in their ongoing battle against cyber threats.
3. Redefining the approach to false positives
Lacework acknowledges that false positives are an inherent aspect of any threat detection system. However, we’ve transformed how these are managed. The platform’s updated user interface, seamlessly integrated within the platform, now provides a feedback mechanism for addressing erroneous detection logic. This allows users to stay in security dashboards, eliminating the need to navigate away to file a support ticket. This direct feedback option in the UI not only streamlines the process but helps Lacework refine detection accuracy across its entire customer base. Moreover, it ensures that teams are equipped with the most pertinent and timely alerts, empowering them to act decisively and effectively.
4. Geographic detection efficacy
New anomaly detection technology from Lacework leverages geographic sources to discover and flag differences in logins and other network connection behaviors. By referencing a user’s latitude and longitude, as well as fuzzy matching the distances between locations, the new geographical enrichment features detect activities outside of typical company behavior and escalate alerts to Lacework dashboards. In this way, a user logging into a company’s cloud from a headquarters in Atlanta, Georgia (the U.S. state) would not be flagged but the same user logging in on the same day from Tbilisi, Georgia (the country) would raise an alert. The level of location-based automation and intelligence enables security teams to respond to suspicious events more swiftly and effectively than ever before.
5. Kubernetes detection expansion
Recognizing the growing importance of containerized applications, Lacework has expanded its threat detection capabilities to Kubernetes (K8s) containers. The new coverage identifies compromised users based on suspicious container activity, and paves the way for future enhancements in scanning Kubernetes environments.
A step forward in cloud threat detection
By harnessing the power of untapped data and integrating advanced AI/ML technologies, Lacework is setting a higher bar in cloud threat detection, with a privacy-first approach which protects your data. This solution empowers security teams to not just react to threats, but proactively manage and mitigate them with early detections. This ensures a safer and more secure cloud environment for customers. This innovative approach is not just about responding to the challenges of today; it’s about being prepared for the evolving threats of tomorrow. These solutions represent an advancement in the way cloud security threats are managed, offering a more intelligent, data-driven approach to keeping cloud environments safe for business operations.
Suggested for you