NginxDay
Lacework Labs Advisory
Lacework Labs Advisory – “Nginx Day”

On Apr 11, 2022 Nginx published a public advisory that both the Open Source and Premium (Nginx Plus) versions are not affected. The security vulnerabilities lie in the Nginx LDAP reference implementation, which if you are using, Nginx has provided configurations to mitigate this vulnerability. At the time of this reporting, no CVE has been assigned to this vulnerability.
According to the Nginx security advisory, the LDAP reference implementation is published as a Python daemon. While the exploit details are currently unclear, it’s presumed that an externally facing daemon would indicate exposure. Lacework Labs performed an analysis of cloud environments we monitor and only uncovered a few instances of this daemon over the past year and have reached out to those who are potentially affected. This indicates a low surface area risk relative to what we observed with Log4j. The following image is an example Lacework event showing reconnaissance against an exposed Nginx LDAP reference implementation. (SSH tag describes the indicator – not the activity):
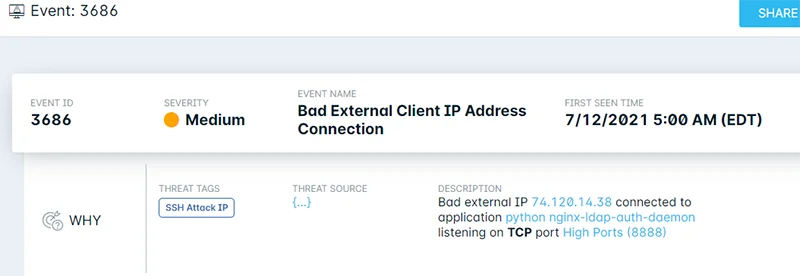
Figure 1. Example Event – Recon against python daemon
Conclusion
In the days of logos and brand names for vulnerabilities, it’s very easy to get caught up in a vicious cycle of never-ending panic. However, collecting available information from the source (Ex: a project’s security announcement page) and identifying what’s known and what’s unknown can help prioritize business decisions and avoid constantly having your SOC burn weekends. Keeping up to date with the countless CVEs is an endless battle. Leveraging vulnerability scanning for hosts, applications, and containers in addition to understanding your public-facing exposure is critical for prioritizing patching decisions.
For content like this and more, be sure to follow us on LinkedIn and Twitter!
Categories
Suggested for you


