Time series model brings another dimension of analysis, uncovering cryptomining threats
Do you know that cryptojacking, also called malicious cryptomining, is now the most popular malware deployed in the cloud? In fact, according to the 2021 Threat Horizons report, a whopping 86% of compromised Google Cloud instances were used for cryptomining and other malicious activities.
Hackers make billions mining Bitcoin and other cryptocurrency by illegally tapping into other people’s computing resources, CPU or GPU, without their knowledge. They not only hack into regular folks’ computers, but they also hack enterprises, retailers, and government agencies to use their high-power servers and machines.
Unlike other attackers, cryptominers flourish by staying covert over a long period of time so they can mine more cryptocurrency. This opens up several attack vectors for criminals to gain control over a company’s cloud infrastructure and data. Once the initial access is established, it can serve as a vehicle for more sophisticated and crippling attacks. Meanwhile, the victims often find that their computers slow down and become impossible to use without realizing what’s going on, and they may suddenly find that their cloud usage costs are through the roof.
As mentioned in our latest blog by Lacework Labs, while cryptojacking is frequently dismissed as an annoyance rather than an actual security incident, it is often co-deployed with additional offensive tooling and can result in severe outcomes. Overlooking cryptojacking is like disregarding someone breaking into your house because they only stole the silverware. But, a typical cloud environment records billions of security signals per month. With so much going on at any moment, how do you even make sense of what’s happening in your cloud environment and choose where to focus?
Proactive, automated threat detection
Given that it is not practical to manually intervene and battle active exploitation in the cloud, a more effective approach to threat detection is a proactive, automated process. However, any technology solution that you use must first understand and learn the normal behavior in your unique environment to flag suspicious or anomalous activities more effectively. The earlier you detect a threat, the better you can minimize the impact of an attack attempt and protect your environment.
This is where unsupervised machine learning models are very helpful. For example, Polygraph®, the Lacework® cloud behavioral analytics engine, uses dozens of models to build a baseline of normal behaviors in your cloud environment. Using your unique baseline, Lacework continuously monitors cloud traffic, events, and processes, then automatically identifies deviations to help you detect known and unknown threats at scale.
In a cryptojacking attack, for example, many new network connections to external servers are launched to download malicious scripts from Bitbucket, GitHub, ngrok.io, etc. to perform coin mining activity, command and control communications, and more. When Lacework detects anomalous connections and activities performed outside of normal context and existing relationships, Lacework generates an alert. When new applications are spawned and there is no prior knowledge about the applications (curl, wget, and malware binaries like kerberods), Polygraph registers it as a new anomaly and triggers an alert.
What is the new capability?
Lacework is introducing a new dimension of analysis based on a time series dataset. This works with the existing cloud behavioral analytics engine to better detect threats like coinminer attacks, compromised accounts, and other unusual activities in the cloud, earlier and efficiently.
The time series model builds a baseline of expected activity frequency and volume in your environment by using past observations to automatically monitor and predict changes over time. These patterns are driven by the needs of our customers. Once we establish a baseline, we continuously monitor your environment to detect spikes and outliers of the volume and frequency of activity in that unique baseline. Unlike signature-based approaches, we don’t simply alert you if the activity frequency or volume goes above a predefined threshold. That could be noisy and ineffective in a dynamic cloud environment and can lead to unnecessary overhead in adjusting thresholds and false positives. Instead, we understand what your normal frequency and volume looks like and can therefore accurately and automatically detect suspicious changes in activities.
How is the time series model different from what the Lacework behavioral analytics engine already does? The Lacework Polygraph behavioral analytics engine continuously monitors new users, applications, network connections, files, etc. in your cloud environment to build a baseline of normal behavior and detect anomalies. Meanwhile, the time series model tracks activity frequency and volume over time for existing entities in the environment to build a baseline of normal activities and detect anomalies through a different lens. Together, they provide a more complete picture of what’s happening in your environment, allowing you to better detect threats before it’s too late. Here is an analogy: think of the Polygraph behavioral analytics engine as cameras outside your home to catch intruders and the new time series analysis as a motion detector or another mechanism on top of the existing cameras to catch suspicious activities quickly and accurately. The key to understanding your threat patterns lies in our Polygraph engine’s ability to learn by looking at your environment using different models and datasets. The more data we collect, the more we can help you detect threats accurately.
How does the time series model help better detect threats?
The Lacework time series model scans cloud-native logs for signs of increased CPU or GPU usage specific to cryptomining operations, misconfigurations, and other unusual cloud usage. It also scans cloud logs for changes in authentication and authorization request volumes and frequency to detect compromised accounts.
- Cryptojacking and resource hijacking: The cloud environments provide a wide attack surface with plenty of CPUs, containers, and virtual machines to exploit. Malicious actors and even insiders can perform mining tasks in the cloud without getting noticed. By monitoring the CPU usage spikes in the cloud-native logs (AWS GPU instances in CloudTrail logs today), and correlating the observations with the baseline and processes running at the time, Lacework can determine if the spike is associated with any planned or known activities, or an indicator of an attack. With this new model, Lacework can now detect these attacks earlier, before the coinminer ramps activity and the costs add up from increased cloud usage.
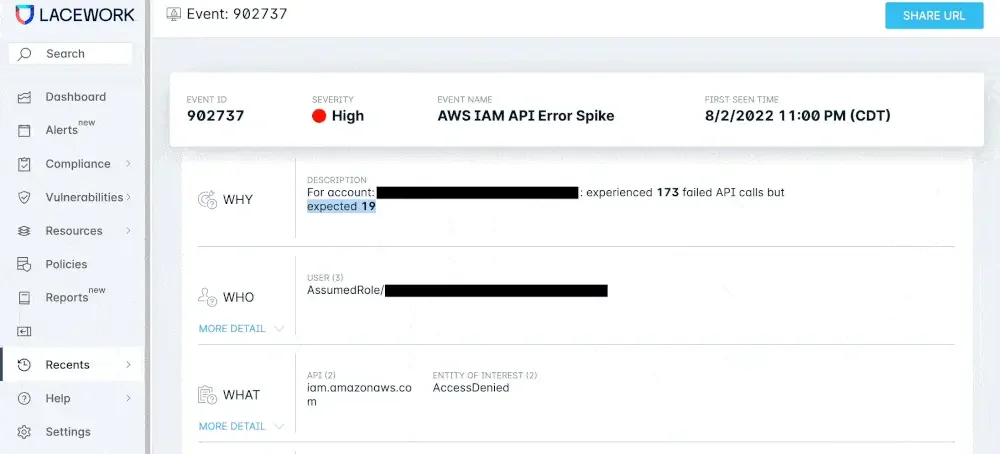
- Compromised accounts: When an attacker attempts to probe an environment to gain information about privileges, permissions, and resources available to a compromised account, it results in a spike in the number of failed authentication and authorization requests. By continuously monitoring the changes in the number and frequency of failed AWS IAM API calls in the CloudTrail logs over time, we can detect potential compromised accounts and alert you.
Misconfigurations or rare, but legitimate, cloud usage: Cloud usage costs are skyrocketing. Often the costs are due to misconfigurations and glitches and sometimes they are due to the legitimate heavy use of cloud applications. But once you are in the cloud, it’s very easy to lose track because static threshold or signature-based methods create many false positives. By continuously monitoring your cloud usage (AWS GPU instances in CloudTrail logs) and understanding how it operates, we build a baseline of expected activity frequency and volume over time for your unique environment. Not only can we understand your normal seasonal changes that you expect at certain times, but we can also correlate the changes with other planned or running activities using multiple analysis methods to alert you about anomalies, so you can address them.
Improved accuracy without too many alerts
Lacework significantly reduces the number of alerts with continuous learning and analysis of activity patterns over time so you can clearly see the spikes relative to your unique baseline. Let’s say we typically see 20-30 failed sign-ins in any given hour in your environment. Suddenly, we detect 1,000 failed sign-ins all at once. We not only help you visualize the spike relative to your baseline, but we consolidate all of those events into one alert so you can investigate potential threats quickly and easily. So, instead of generating 1,000 alerts that could easily overwhelm your resource-constrained teams, Lacework provides one high-quality alert with rich context to help you understand the 5 Ws: the why, who, what, when, and where. Lacework also automatically adjusts the severity of alerts based on continuous learning and a fine-grained understanding of how much the observed behaviors deviate from the predicted baseline for improved accuracy.
The challenge to find the right insights or critical deviations in the midst of billions of signals is not unique to any specific industry –- every business struggles to have that data before it’s too late. No one model fits all! By combining different machine language models that analyze contextually relevant signals, Lacework surfaces the real threats specific to your unique environment. And because many of these signals that we use are collected over time (e.g., daily number of failed sign-ins, increase in the number of launched GPU instances for an account, etc.), time series models can be particularly helpful in combating a broad range of threats in the cloud. Not only do we successfully self-learn and adjust analysis to provide you accurate alerts, but we also capture critical information that you were missing before to help you better understand your environment.
Suggested for you