Visualize and prioritize risks with Lacework Explorer
Lacework Explorer is a tool that puts you in the center of your cloud footprint’s backyard. It visualizes risk entities across your cloud environment and shows how each is related to one another. In this way, Lacework Explorer gives security teams the ability to assess how threats can move laterally among risks, prioritize remediation, and take the necessary steps to quickly improve their security posture.

With Lacework Explorer, users can query data related to their cloud footprint and explore answers in a clear, visual network representation. The graph shows resources, associated relationships, and how threats can interact among them. With the feature, security professionals gain insight into how connected resources could be affected in an attack; how wide a potential blast radius could be; how exposed secrets and/or internet exposure could enable lateral movement; and more.
How does it work?
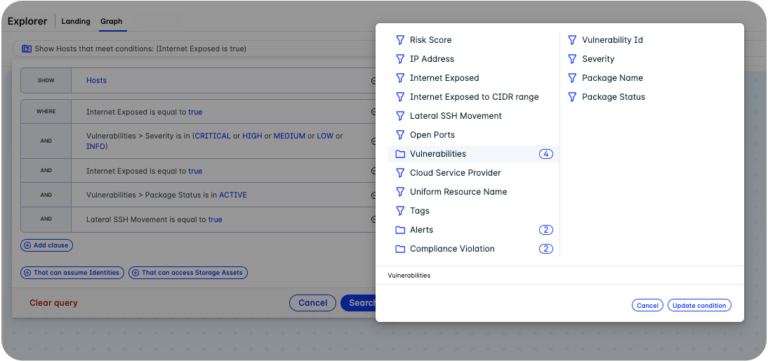
Explorer queries in action
A big part of Lacework Explorer’s enhanced utility comes through a new, natural language query builder, which allows users to customize and pivot their research with predefined prompts. Users can then investigate different entity types with virtually any number of associated conditions. Queries can include language such as:
- Show me all data sources to which identity x has access
- Show me all compute instances that are internet-exposed, have critical or high vulns, and can reach this specific data resource
- Show me all internet-exposed instances with active package vulnerabilities
- Show me all the resources that a specific identity has access to such as S3, compute engines, IAM roles, blob storage, KMS, and RDS
Lacework Explorer provides a multi-dimensional view that shows multiple orders of relationships (for example, it shows the potential lateral movement an attacker can take via an exposed secret or an overly permissive role) and how each entity in that chain could affect another.
Thanks to the visual approach and intuitive querying capabilities of Lacework Explorer, teams can now save time when it comes to identifying, contextualizing, and remediating risks.
Lacework Explorer in action
Let’s see how using Lacework Explorer could enhance your job as a SOC analyst. Imagine you’re on a team at a rapidly-growing e-commerce startup. Until recently, the company ran its web presence out of an old Windows server stored in the back room of the company. However, as site traffic and transactions have grown, the team scaled into the cloud with a basic Amazon EC2 instance. That cloud server processes thousands of transactions each day and handles sensitive information such as customer credit card numbers and addresses.
One day, your team gets an urgent message from leadership asking whether anyone has accessed the EC2 instance from Colombo, Sri Lanka and whether the Lacework GeoIP-based Composite Alert that he received was legitimate. The team, which hasn’t left HQ in three days, immediately knows that someone is trying to break into — or has broken into — the company’s server.
With Lacework Explorer, you quickly hone in on the EC2 instance that’s associated with the Identity and Access Management (IAM) role running the web presence for the company. From here, it’s easy to see that the EC2 instance related to the IAM role has 14 potential issues, including four known vulnerabilities, seven misconfigurations, and three SSH secrets. Each of those issues is visually mapped to the EC2 instance under scrutiny and to the parent IAM role configuring the server, indicating that the team needs to pay special attention to the potentially compromised IAM role.
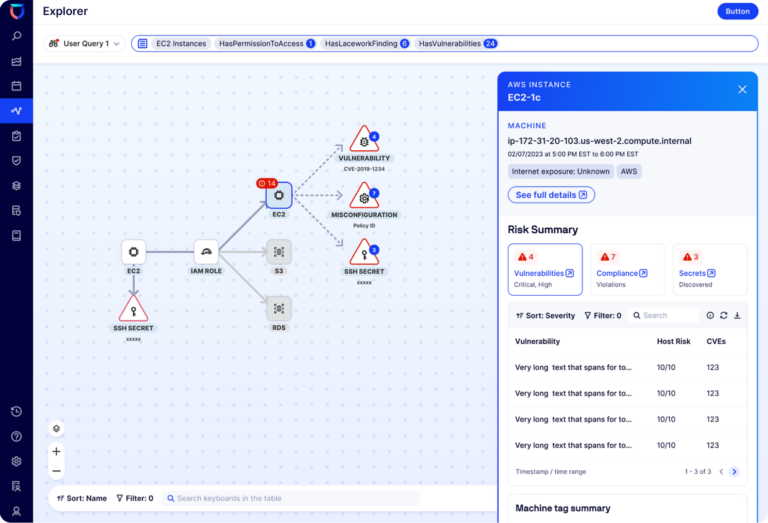
Lacework Explorer showing the relationship among IAM roles, EC2 instances, and risks
This visibility into excessive privileges provided by Lacework Explorer gives the team what it needs to continue remediation. At this point, the team prepares documentation and informs the broader company that there’s potential for this threat actor to move from the EC2 instance to crown jewel assets like S3 buckets managed by this IAM role.
Clicking into the EC2 instance and selecting the misconfiguration section, you see that, among the misconfigurations, an uncommon port is open to web traffic. Cross-checking that with the company firewall, it’s evident that this port has not been blocked by that line of defense, opening up the opportunity for a malicious actor to access the server.
Luckily, none of the team’s EC2 credentials were compromised and the geo-IP Lacework alert flagged the intrusion before any damage was done. Using Lacework Explorer as a reference, your team logs into AWS, reconfigures the port, and ensures that no traffic can reach the company’s server through that channel.
Save time and resources
Lacework Explorer saves security teams time and resources by visualizing cloud entities and showing how each is related. For Lacework customers looking to streamline their operations, this tool brings exciting value.
Categories
Suggested for you


